Hashcat初体验教程
Hashcat初体验
支持的HASH
1 |
|
完整hash示例列表
使用
下载
Windows下载hashcat
Linux下载hashcat
1 | apt install hashcat |
参数详情
| 参数 | 类型 | 描述 | 示例 |
|---|---|---|---|
-m, --hash-type |
数字 | 哈希类型,参考Mode,可破解的格式(否则自动检测) | -m 1000 |
-a, --attack-mode |
数字 | 攻击模式,见下方参考内容 | -a 3 |
-V, --version |
无 | 打印版本信息 | |
-h, --help |
无 | 打印帮助信息 | |
--quiet |
无 | 抑制输出 | |
--hex-charset |
无 | 假定字符集以十六进制形式给出 | |
--hex-salt |
无 | 假定盐值以十六进制形式给出 | |
--hex-wordlist |
无 | 假定单词列表中的单词以十六进制形式给出 | |
--force |
无 | 忽略警告信息 | |
--deprecated-check-disable |
无 | 启用已弃用的插件 | |
--status |
无 | 启用状态屏幕的自动更新 | |
--status-json |
无 | 启用状态输出的 JSON 格式 | |
--status-timer |
数字 | 将状态屏幕更新间隔设置为 X 秒 | --status-timer=1 |
--stdin-timeout-abort |
数字 | 如果标准输入在 X 秒内无输入则中止操作 | --stdin-timeout-abort=300 |
--machine-readable |
无 | 以机器可读的格式显示状态视图 | |
--keep-guessing |
无 | 在哈希被破解后继续猜测 | |
--self-test-disable |
无 | 在启动时禁用自检功能 | |
--loopback |
无 | 将新的明文添加到导入目录 | |
--markov-hcstat2 |
文件 | 指定要使用的 hcstat2 文件 | --markov-hcstat2=my.hcstat2 |
--markov-disable |
无 | 禁用马尔可夫链,模拟经典的暴力破解 | |
--markov-classic |
无 | 启用经典马尔可夫链(无逐位置功能) | |
--markov-inverse |
无 | 启用逆马尔可夫链(无逐位置功能) | |
-t, --markov-threshold |
数字 | 当达到阈值 X 时,停止接受新的马尔可夫链 | -t 50 |
--runtime |
数字 | 运行 X 秒后中止会话 | --runtime=10 |
--session |
字符串 | 定义特定的会话名称 | --session=mysession |
--restore |
无 | 从 “–session” 恢复会话 | |
--restore-disable |
无 | 不写入恢复文件 | |
--restore-file-path |
文件 | 恢复文件的特定路径 | --restore-file-path=x.restore |
-o, --outfile |
文件 | 为恢复的哈希定义输出文件 | -o outfile.txt |
--outfile-format |
字符串 | 要使用的输出文件格式,以逗号分隔 | --outfile-format=1,3 |
--outfile-autohex-disable |
无 | 禁用在输出明文中使用 “$HEX []” | |
--outfile-check-timer |
数字 | 将输出文件检查间隔设置为 X 秒 | --outfile-check-timer=30 |
--wordlist-autohex-disable |
无 | 禁用从单词列表中转换 “$HEX []” | |
-p, --separator |
字符 | 哈希列表和输出文件的分隔字符 | -p : |
--stdout |
无 | 不破解哈希,仅打印候选内容 | |
--show |
无 | 比较哈希列表和密码本文件,显示已破解的哈希 | |
--left |
无 | 比较哈希列表和密码本文件,显示未破解的哈希 | |
--username |
无 | 启用在哈希文件中忽略用户名的功能 | |
--remove |
无 | 启用在哈希被破解后将其删除的功能 | |
--remove-timer |
数字 | 每 X 秒更新一次输入的哈希文件 | --remove-timer=30 |
--potfile-disable |
无 | 不写入密码本文件 | |
--potfile-path |
文件 | 密码本文件的特定路径 | --potfile-path=my.pot |
--encoding-from |
编码 | 强制将内部单词列表编码从 X 转换 | --encoding-from=iso-8859-15 |
--encoding-to |
编码 | 强制将内部单词列表编码转换为 X | --encoding-to=utf-32le |
--debug-mode |
数字 | 定义调试模式(仅在使用规则时为混合模式) | --debug-mode=4 |
--debug-file |
文件 | 用于调试规则的输出文件 | --debug-file=good.log |
--induction-dir |
目录 | 指定用于回环的导入目录 | --induction=inducts |
--outfile-check-dir |
目录 | 指定用于监控明文的输出文件目录 | --outfile-check-dir=x |
--logfile-disable |
无 | 禁用日志文件 | |
--hccapx-message-pair |
数字 | 仅加载与 X 匹配的 hccapx 消息对 | --hccapx-message-pair=2 |
--nonce-error-corrections |
数字 | 用于替换 AP 随机数最后字节的暴力破解大小范围 | --nonce-error-corrections=16 |
--keyboard-layout-mapping |
文件 | 用于特殊哈希模式的键盘布局映射表 | --keyb=german.hckmap |
--truecrypt-keyfiles |
文件 | 要使用的 TrueCrypt 密钥文件,以逗号分隔 | --truecrypt-keyf=x.png |
--veracrypt-keyfiles |
文件 | 要使用的 VeraCrypt 密钥文件,以逗号分隔 | --veracrypt-keyf=x.txt |
--veracrypt-pim-start |
数字 | VeraCrypt 个人迭代乘数的起始值 | --veracrypt-pim-start=450 |
--veracrypt-pim-stop |
数字 | VeraCrypt 个人迭代乘数的结束值 | --veracrypt-pim-stop=500 |
-b, --benchmark |
无 | 对所选哈希模式运行基准测试 | |
--benchmark-all |
无 | 对所有哈希模式运行基准测试(需要 “-b” 选项) | |
--speed-only |
无 | 返回预期的攻击速度,然后退出 | |
--progress-only |
无 | 返回理想的进度步长以及处理所需时间 | |
-c, --segment-size |
数字 | 将从单词文件缓存的大小(以 MB 为单位)设置为 X | -c 32 |
--bitmap-min |
数字 | 将位图允许的最小位数设置为 X | --bitmap-min=24 |
--bitmap-max |
数字 | 将位图允许的最大位数设置为 X | --bitmap-max=24 |
--cpu-affinity |
字符串 | 锁定到 CPU 设备,以逗号分隔 | --cpu-affinity=1,2,3 |
--hook-threads |
数字 | 为钩子(每个计算单元)设置线程数量 | --hook-threads=8 |
--hash-info |
无 | 显示每个哈希模式的相关信息 | |
--example-hashes |
无 | “–hash-info” 的别名 | |
--backend-ignore-cuda |
无 | 在启动时不尝试打开 CUDA 接口 | |
--backend-ignore-hip |
无 | 在启动时不尝试打开 HIP 接口 | |
--backend-ignore-metal |
无 | 在启动时不尝试打开 Metal 接口 | |
--backend-ignore-opencl |
无 | 在启动时不尝试打开 OpenCL 接口 | |
-I, --backend-info |
无 | 显示系统 / 环境 / 后端 API 信息 | -I或-II |
-d, --backend-devices |
字符串 | 要使用的后端设备,以逗号分隔 | -d 1 |
-D, --opencl-device-types |
字符串 | 要使用的 OpenCL 设备类型,以逗号分隔 | -D 1 |
-O, --optimized-kernel-enable |
无 | 启用优化内核(限制密码长度) | |
-M, --multiply-accel-disable |
无 | 禁用与处理器数量相关的乘法内核加速 | |
-w, --workload-profile |
数字 | 启用特定的工作负载配置文件,见下方说明 | -w 3 |
-n, --kernel-accel |
数字 | 手动调整工作负载,将外循环步长设置为 X | -n 64 |
-u, --kernel-loops |
数字 | 手动调整工作负载,将内循环步长设置为 X | -u 256 |
-T, --kernel-threads |
数字 | 手动调整工作负载,将线程数量设置为 X | -T 64 |
--backend-vector-width |
数字 | 手动覆盖后端向量宽度为 X | --backend-vector=4 |
--spin-damp |
数字 | 使用 CPU 进行设备同步,以百分比表示 | --spin-damp=10 |
--hwmon-disable |
无 | 禁用温度和风扇转速的读取及触发功能 | |
--hwmon-temp-abort |
数字 | 如果温度达到 X 摄氏度则中止操作 | --hwmon-temp-abort=100 |
--scrypt-tmto |
数字 | 手动覆盖 Scrypt 的 TMTO 值为 X | --scrypt-tmto=3 |
-s, --skip |
数字 | 从开头跳过 X 个单词 | -s 1000000 |
-l, --limit |
数字 | 限制从开头开始(包含已跳过的单词)的 X 个单词 | -l 1000000 |
--keyspace |
无 | 显示密钥空间的基数:模数 值并退出 | |
-j, --rule-left |
规则 | 将单个规则应用于左侧单词列表中的每个单词 | -j 'c' |
-k, --rule-right |
规则 | 将单个规则应用于右侧单词列表中的每个单词 | -k '^-' |
-r, --rules-file |
文件 | 将多个规则应用于单词列表中的每个单词 | -r rules/best64.rule |
-g, --generate-rules |
数字 | 生成 X 个随机规则 | -g 10000 |
--generate-rules-func-min |
数字 | 强制每个规则最少包含 X 个函数 | |
--generate-rules-func-max |
数字 | 强制每个规则最多包含 X 个函数 | |
--generate-rules-func-sel |
字符串 | 随机规则引擎有效的规则操作符集合 | --generate-rules-func-sel=ioTlc |
--generate-rules-seed |
数字 | 强制将随机数生成器种子设置为 X | |
-1, --custom-charset1 |
字符集 | 用户定义的字符集 1 | -1?l?d?u |
-2, --custom-charset2 |
字符集 | 用户定义的字符集 2 | -2?l?d?s |
-3, --custom-charset3 |
字符集 | 用户定义的字符集 3 | |
-4, --custom-charset4 |
字符集 | 用户定义的字符集 4 | |
--identify |
无 | 显示输入哈希支持的所有算法 | --identify my.hash |
--increment |
无 | 启用掩码增量模式 | |
--increment-min |
数字 | 从 X 开始进行掩码增量 | --increment-min=4 |
--increment-max |
数字 | 在 X 处停止进行掩码增量 | --increment-max=8 |
--slow-candidates |
无 | 启用更慢(但更高级)的候选生成器 | |
--brain-server |
无 | 启用大脑服务器 | |
--brain-server-timer |
数字 | 每 X 秒(最少 60 秒)更新一次大脑服务器转储内容 | --brain-server-timer=300 |
--brain-client |
无 | 启用大脑客户端,激活 “-S” 选项 | |
--brain-client-features |
数字 | 定义大脑客户端功能,见下方说明 | --brain-client-features=3 |
--brain-host |
字符串 | 大脑服务器主机(IP 或域名) | --brain-host=127.0.0.1 |
--brain-port |
端口 | 大脑服务器端口 | --brain-port=13743 |
--brain-password |
字符串 | 大脑服务器认证密码 | --brain-password=bZfhCvGUSjRq |
--brain-session |
十六进制 | 覆盖自动计算的大脑会话 | --brain-session=0x2ae611db |
--brain-session-whitelist |
十六进制 | 仅允许给定的会话,以逗号分隔 | --brain-session-whitelist=0x2ae611db |
Attack Modes
(-a, --attack-mode)
| Mode | 描述 | |
|---|---|---|
| 0 | Straight | 直接攻击,也就是字典攻击 |
| 1 | Combination | 组合攻击,组合多个字典进行攻击 |
| 3 | Brute-force/ Mask | 暴力破解/掩码(Built-in charsets) |
| 6 | Hybrid Wordlist + Mask | 结合单词列表与掩码的混合模式,综合两者优势来运作。 |
| 7 | Hybrid Mask + Wordlist | 与 6 类似,但顺序上是先掩码后结合单词列表的混合模式。 |
| 9 | Association | 关联攻击,特定情况下,极快 |
Built-in charsets
-1, --custom-charset1、-2, --custom-charset2、-3, --custom-charset3、-4, --custom-charset4
(暴力破解和掩码攻击的内置字符集,你也可以进行自己定制,参数有介绍)
| Charset | Representation |
|---|---|
| ?l | abcdefghijklmnopqrstuvwxyz [a-z] |
| ?u | ABCDEFGHIJKLMNOPQRSTUVWXYZ [A-Z] |
| ?d | 0123456789 [0-9] |
| ?h | 0123456789abcdef [0-9a-f] |
| ?H | 0123456789ABCDEF [0-9A-F] |
| ?s | !”#$%&’()*+,-./:;<=>?@[]^_`{}~ |
| ?a | ?l?u?d?s |
| ?b | 0x00 - 0xff |
OpenCL Device Types
(-D, --opencl-device-types) 设备类型
| # | Device Type |
|---|---|
| 1 | CPU |
| 2 | GPU |
| 3 | FPGA, DSP, Co-Processor |
Outfile Formats
(--outfile-format)需要 -o
| # | 格式 | |
|---|---|---|
| 1 | hash[:salt] | 哈希 [: 盐值] |
| 2 | plain | 明文 |
| 3 | hex_plain | 十六进制明文 |
| 4 | crack_pos | 破解位置 |
| 5 | timestamp absolute | 绝对时间戳 |
| 6 | timestamp relative | 相对时间戳 |
Rule Debugging Modes
| # | 格式 | |
|---|---|---|
| 1 | Finding-Rule | 查找规则 |
| 2 | Original-Word | 原始单词 |
| 3 | Original-Word:Finding-Rule | 原始单词:查找规则 |
| 4 | Original-Word:Finding-Rule:Processed-Word | 原始单词:查找规则:处理后的单词 |
| 5 | Original-Word:Finding-Rule:Processed-Word:Wordlist | 原始单词:查找规则:处理后的单词:单词表 |
Brain Client Features
(--brain-client-features)分布式客户端功能
| # | Features | |
|---|---|---|
| 1 | Send hashed passwords | 发送哈希密码 |
| 2 | Send attack positions | 发送攻击位置 |
| 3 | Send hashed passwords and attack positions | 发送哈希密码和攻击位置 |
Workload Profiles
(-w, --workload-profile工作负载配置)
| # | 性能 | 运行时间 | 功耗 | 桌面影响 | |
|---|---|---|---|---|---|
| 1 | Low | 2 ms | Low | Minimal | 性能低、运行时间 2 毫秒、功耗低、对桌面影响极小 |
| 2 | Default | 12 ms | Economic | Noticeable | 性能默认、运行时间 12 毫秒、功耗经济、有明显影响 |
| 3 | High | 96 ms | High | Unresponsive | 性能高、运行时间 96 毫秒、功耗高、无响应(桌面卡顿严重) |
| 4 | Nightmare | 480 ms | Insane | Headless | 性能极高(堪称噩梦级)、运行时间 480 毫秒、功耗极高、无桌面交互(类似无头模式) |
常用参数
-h, --help帮助信息
-V, --version版本信息

-I, --backend-info显示系统环境
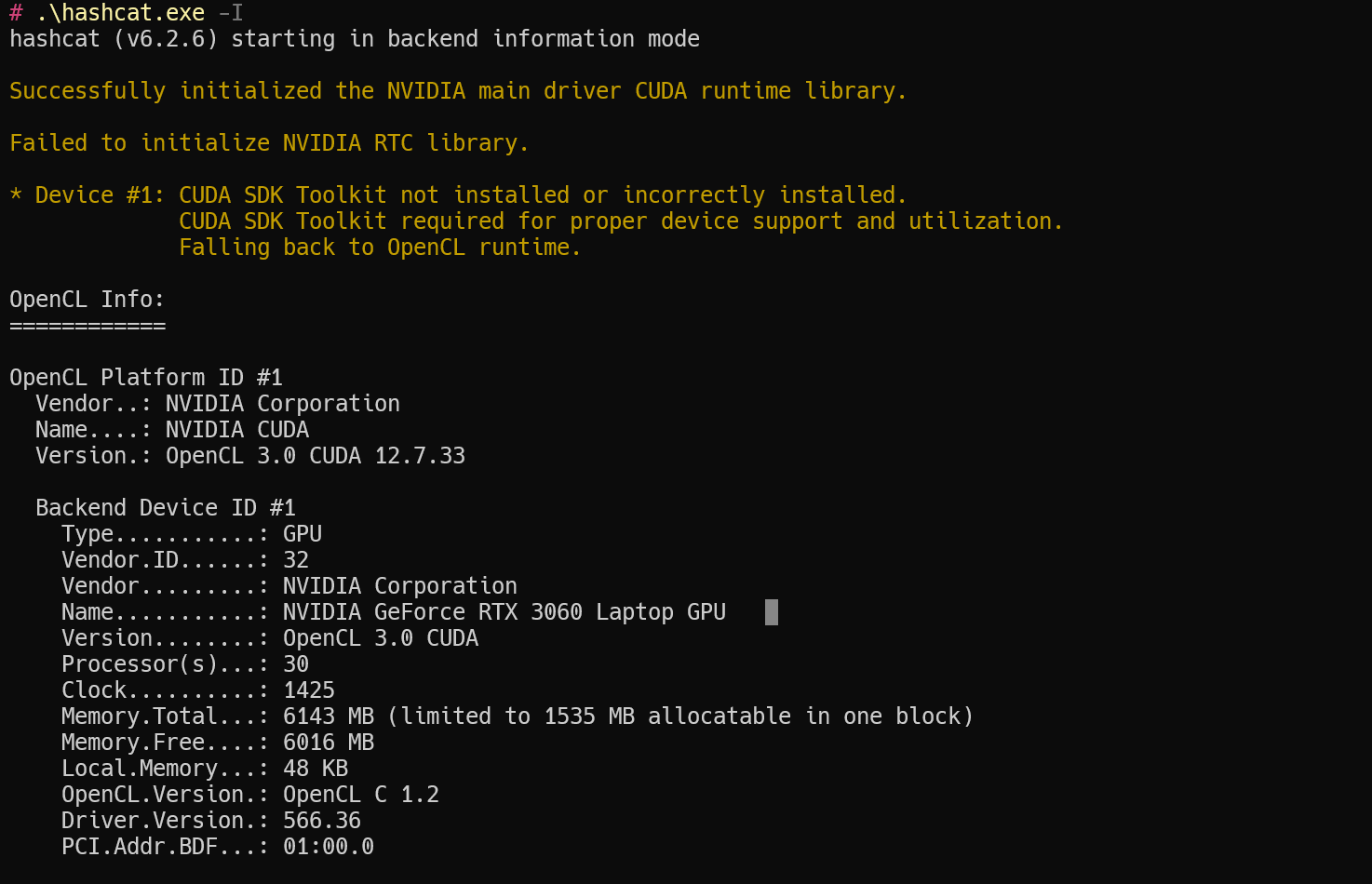
-b, --benchmark对hash进行基准测试,可以单选特定hash,也可以进行全部测试
-a, --attack-mode攻击方式详情见Attack Modes

参数使用方式(#为0-9)
1 | hashcat -a # |
详细示例
-a 0(直接模式,也就是字典破解)
1 | hashcat -a 0 -m 0 0192023a7bbd73250516f069df18b500 "E:\400W常用密码(整理).txt" |
-a 1(组合攻击)
1 | hashcat -a 1 -m 0 0192023a7bbd73250516f069df18b500 "E:\400W常用密码(整理).txt" "E:\400W常用密码(整理)2.txt" |
例:
E:\400W常用密码(整理).txt
1 | pass |
E:\400W常用密码(整理)2.txt
1 | alice |
组合的密码就是
1 | passalice |
也可以使用相同的字典
1 | hashcat -a 1 -m 0 0192023a7bbd73250516f069df18b500 "E:\400W常用密码(整理).txt" "E:\400W常用密码(整理).txt" |
组合生成的密码是
1 | passpass |
扩展:
也可以将规则应用于字典中
1 | -j, --rule-left=RULE 将单个规则应用于左侧单词列表中的每个单词 |
字典1
1 | yellow |
字典2
1 | car |
命令为
1 | hashcat -a 1 -m 0 0192023a7bbd73250516f069df18b500 "字典1.txt" "字典2.txt" -j '$-' -k '$!' |
生成的字典为
1 | yellow-car! |
命令中的引号只是用来转义$符号的,因为有些情况会将$-在shell中解释为变量,在每个操作系统和每个shell解释器转义都不相同,建议查找操作系统和shell解释器手册
并且,在官方文档中有一句提示
1 | 你可能会看到,在Hashcat的状态中,其中一个字典被标记为“base”(攻击的核心基础),而另一个被标记为“mod”(应用于攻击的“修饰符”)。Hashcat会根据文件的相对大小,动态地内部决定哪个是“base”,哪个是“mod”,以提高效率。这是用户无法干预的,且不会影响输出结果(只会影响速度)。 |
-a 3在官方文档中,暴力攻击已经过时,被掩码攻击所替代,所以 Brute-force/ Mask 就是掩码攻击
字符集已经在上述说明,可以查看Built-in charsets
现在说一下自定义字符集
1 | --custom-charset1=CS |
上述字符集都有快捷方式
-1、-2、-3、-4
例
以下都生成了字符abcdefghijklmnopqrstuvwxyz0123456789相同字符集,在自定义字符集时可以在其中使用内置字符集参数
1 | -1 abcdefghijklmnopqrstuvwxyz0123456789 |
再说以下常见的组合方式
| 掩码 | 结果 |
|---|---|
| ?d?d?d?d?d?d | 6位纯数字 |
| ?u?l?l?s?d?d?d?d | 大写+两小写+特殊字符+4位数字 |
| ms?u?l?l?s?d?d?d?d | 前两位时ms后面同上 |
| ?u?l?l?s?d?d?d?dms | 后两位时ms前面同上 |
以此类推即可
Hashcat还有字符集文件(.hcchr)及掩码文件(.hcmask)
字符集文件:方便重复使用字符集,使用自定义字符集,支持使用Hashcat提供的语言特定字符集
提示:使用 iconv 和类似工具将文件转换为特定语言的文件编码
掩码文件:就是将高效的掩码组合放在一个文件中使用
通用格式
1 | [?1,][?2,][?3,][?4,]mask |
[?1]:第 1 个自定义字符集(--custom-charset1或-1)将被设置为该值,可选。[?2]:第 2 个自定义字符集(--custom-charset2或-2)将被设置为该值,可选。[?3]:第 3 个自定义字符集(--custom-charset3或-3)将被设置为该值,可选。[?4]:第 4 个自定义字符集(--custom-charset4或-4)将被设置为该值,可选。[mask]:掩码,可以使用由[?1]、[?2]、[?3]或[?4]定义的自定义字符集,也可以使用任何预定义的字符集(如?l、?u、?d、?h、?H、?s、?a、?b),还可以包含固定字符(示例值:pass?1?d?d?2?l?l)。
1 | 例: |
hashcat有一些示例文件,在mask文件夹中
使用掩码文件
1 | hashcat -m 0 -a 3 0192023a7bbd73250516f069df18b500 my.hcmask |
掩码增量
--increment指掩码长度不固定,但应增加长度
--increment-min掩码最小长度(如使用--increment而未指定--increment-min则默认为1)
--increment-max掩码最大长度(如使用--increment而未指定--increment-max则默认掩码指定长度)
1 | hashcat -m 0 -a 3 --increment --increment-min 4 --increment-max 6 0192023a7bbd73250516f069df18b500 ?a?a?a?a?a?a?a?a |
-m 0:我们将哈希类型设置为 MD5Hash类型-a 3:设置攻击模式为掩蔽攻击Attack Modes--increment:启用增量模式参数详情--increment-min 4:将候选密码的最小长度设置为 4参数详情--increment-max 6:将候选密码的最大长度设置为 6参数详情?a?a?a?a?a?a?a?a:掩码是内置字符集 ?a(“all”,包括大小写字符、数字和特殊字符)的 8 个字符长的字符串Built-in charsets
任何情况下,掩码攻击中,掩码都是必须的
-a 6 和 -a 7(混合攻击)
混合攻击就是组合攻击,只不过一侧是字典,另一侧时掩码
-a 6
例:
1 | hashcat -m 0 -a 6 0192023a7bbd73250516f069df18b500 字典1.txt ?d?d?d?d |
字典1
1 | password |
生成结果为
1 | password0000 |
-a 7即为-a 6的相反
例:
1 | hashcat -m 0 -a 7 0192023a7bbd73250516f069df18b500 ?d?d?d?d 字典1.txt |
生成结果为
1 | 0000password |
扩展:
[hybrid_atttack_with_rules hashcat wiki]
-a 9(关联攻击)
- 你有一个大型的加盐哈希列表。
- 同时,你对哈希列表中的每个哈希都有一些“提示”或“信息”
关联攻击,它只对hash表中,每个hash使用的关联信息进行攻击
使用场景
- 慢速单哈希攻击:如果你想用单个单词加上一些规则来攻击一个慢速的单哈希,可以使用大写的
-S参数。 - 多词表支持:虽然这与攻击的效率相悖,但在某些情况下,使用多个词表是有意义的。例如,如果密码中有大量子字符串是后来添加的(如 Yubikey 按键生成的字符串、站点特定的字符串或用户使用的公司名称)。
构建测试数据集:首先创建一个包含用户名和哈希的测试数据集。
1
2
3
4
5$ head -10000 example.dict > wordlist.txt
$ shuf wordlist.txt | sponge wordlist.txt
$ tools/test.pl passthrough 3200 < wordlist.txt > hashlist.txt
$ perl -e 'open (IN, "wordlist.txt"); my @a = <IN>; close (IN); open (IN, "hashlist.txt"); my @b = <IN>; close (IN); for (my $i = 0; $i < scalar @a; $i++) { chomp $a[$i]; chomp ($b[$i]); printf ("%s:%s\n", $a[$i], $b[$i]); } print scalar @b' > final.txt
$ rm wordlist.txt hashlist.txt拆分数据集:将用户名和哈希分开,以便使用新的攻击模式。
1
2$ cut -d: -f1 < final.txt > wordlist.txt
$ cut -d: -f2 < final.txt > hashlist.txt传统攻击模式:使用传统的
-a 0攻击模式,观察所需时间。1
$ ./hashcat -m 3200 hashlist.txt wordlist.txt -o result.txt
结果可能需要数小时才能完成。
新攻击模式:使用新的
-a 9攻击模式。1
$ ./hashcat -m 3200 hashlist.txt wordlist.txt -o result.txt -a 9
结果在几秒钟内就能完成,因为它直接使用了与哈希关联的用户名作为密码。
特殊的攻击方式(基于规则攻击 -a 0 -r)
只是简单介绍一下,具体规则如何编写,查看官方文档rule_based_attack hashcat wiki
可以有一个或多个规则组成,是所有攻击中最为复杂的一种
1 | cat 123.rule //规则1 |
-m, --hash-type哈希类型,参考HASH列表
示例
1 | hashcat.exe -a 0 -m 0 8914de686ab28dc22f30d3d8e107ff6c "E:\400W常用密码(整理).txt" |
-m 0代表为md5,如果不指定默认也为md5
-o, --outfile为破解完的hash保存到指定位置
示例
1 | hashcat -a 0 -m 0 8914de686ab28dc22f30d3d8e107ff6c "E:\400W常用密码(整理).txt" -o test.txt |
--status启用屏幕自动更新
输入这个后就不会出现一下情况
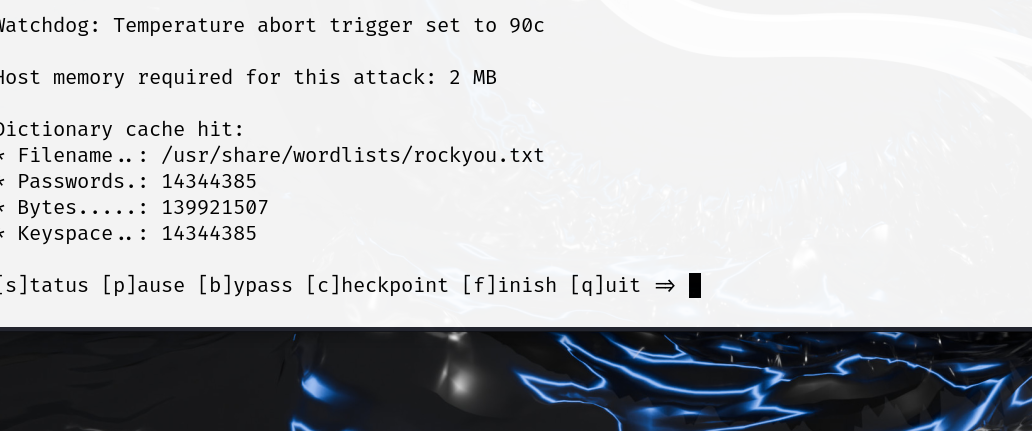
不许要手动按s即可自动更新
--hash-info显示每个哈希模式的相关信息
一般情况下推荐官方网站查询hashcat wiki
--machine-readable以机器可读方式显示

--potfile-disable不将破解成功的密码写入hashcat.potfile文件
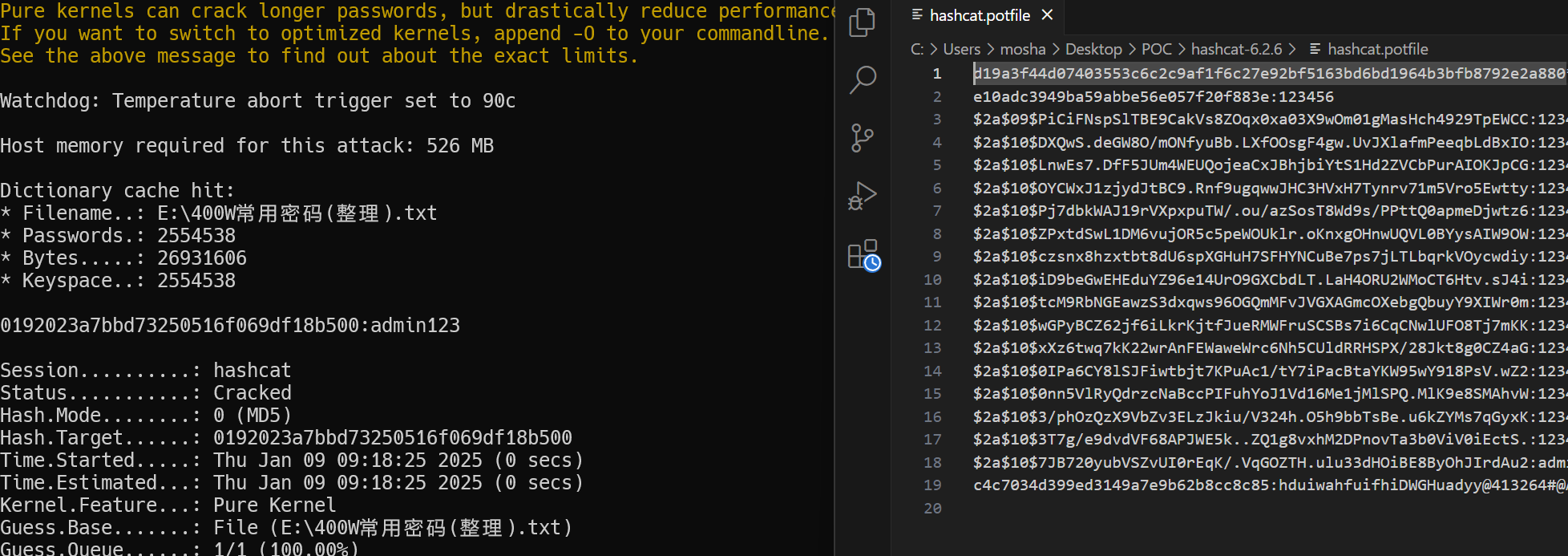
这样下次就可以重复破解,如果已经破解成功且没有加此参数可以删除hashcat.potfile文件内的内容
--show在未启用–potfile-disable的情况下,可以显示破解过的hash
下面是破解后未加--show
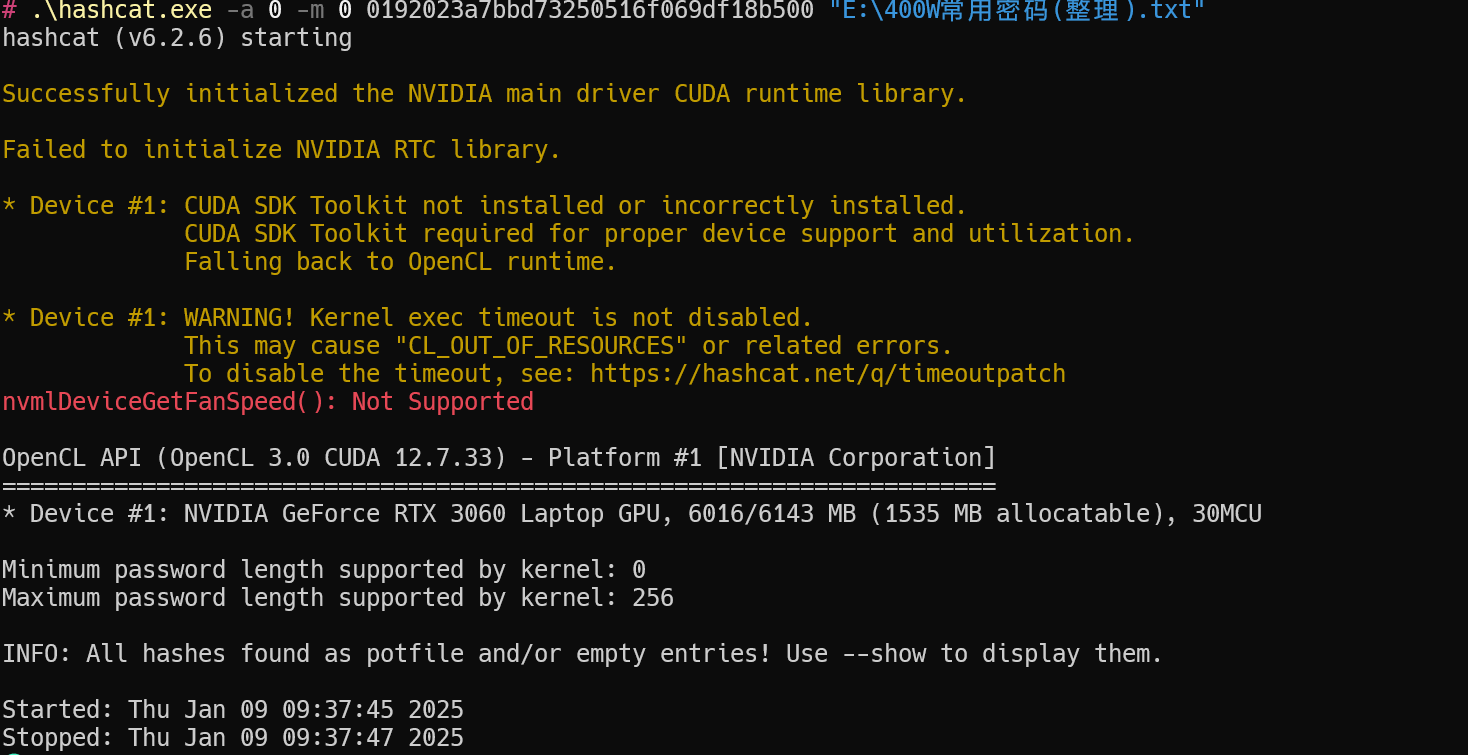
下面是加了--show

--show(必需)- 哈希类型(可选,例如
-m 0是默认值) - pot 文件路径(
--potfile-path,可选):指定一个特定的输入.potfile(包含之前的破解结果) - 用户名(
--username,可选):告诉 hashcat 哈希文件的每一行的第一个字段是用户名或电子邮件地址 - 输出文件(
--outfile或-o,可选):存储输出的文件 - 输出格式(
--outfile-format,参见--help了解可能的值,可选):更改输出的显示方式,例如仅显示密码、以十六进制显示密码、不显示哈希等 - 安静模式(
--quiet,可选):启用安静模式(不显示任何额外信息) - 原始哈希文件(必需):这需要是未修改的哈希列表,
--remove会修改或删除哈希文件中的哈希
-O, --optimized-kernel-enable开启内核优化,密码长度限制在32位
-w, --workload-profile启动特定的工作负载文件
-D, --opencl-device-types使用opencl设备类型
此选项时设备类型详见OpenCL Device Types
-d, --backend-devices要使用的后端设备
此选项时选择设备
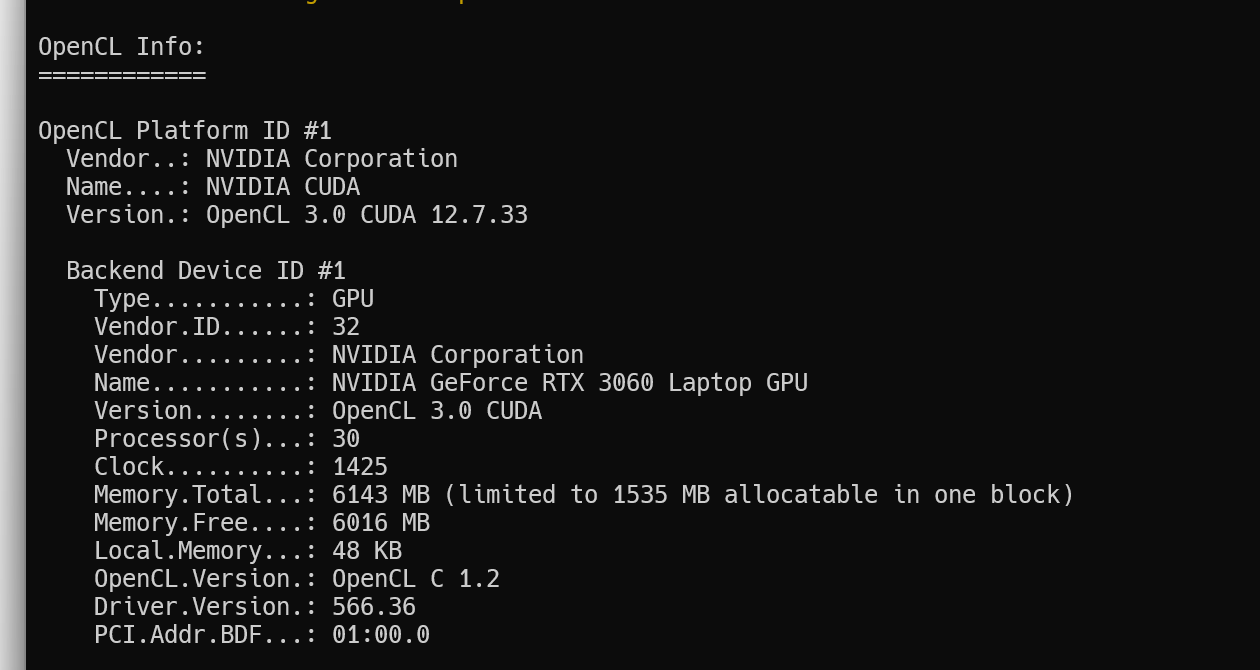
不选择时,默认位所有设备工作
--session和--restore保存和恢复
1 | hashcat -a 0 -m 0 8914de686ab28dc22f30d3d8e107ff6c "E:\400W常用密码(整理).txt" --session test |
恢复
1 | hashcat.exe --sessio test --restore |
常见爆破
本次示例都以字典破解为例,其他实验可以自行尝试
小技巧
1 | hashcat xxxxxxx //x为hash的值可以让hashcat判断它属于什么加密 |
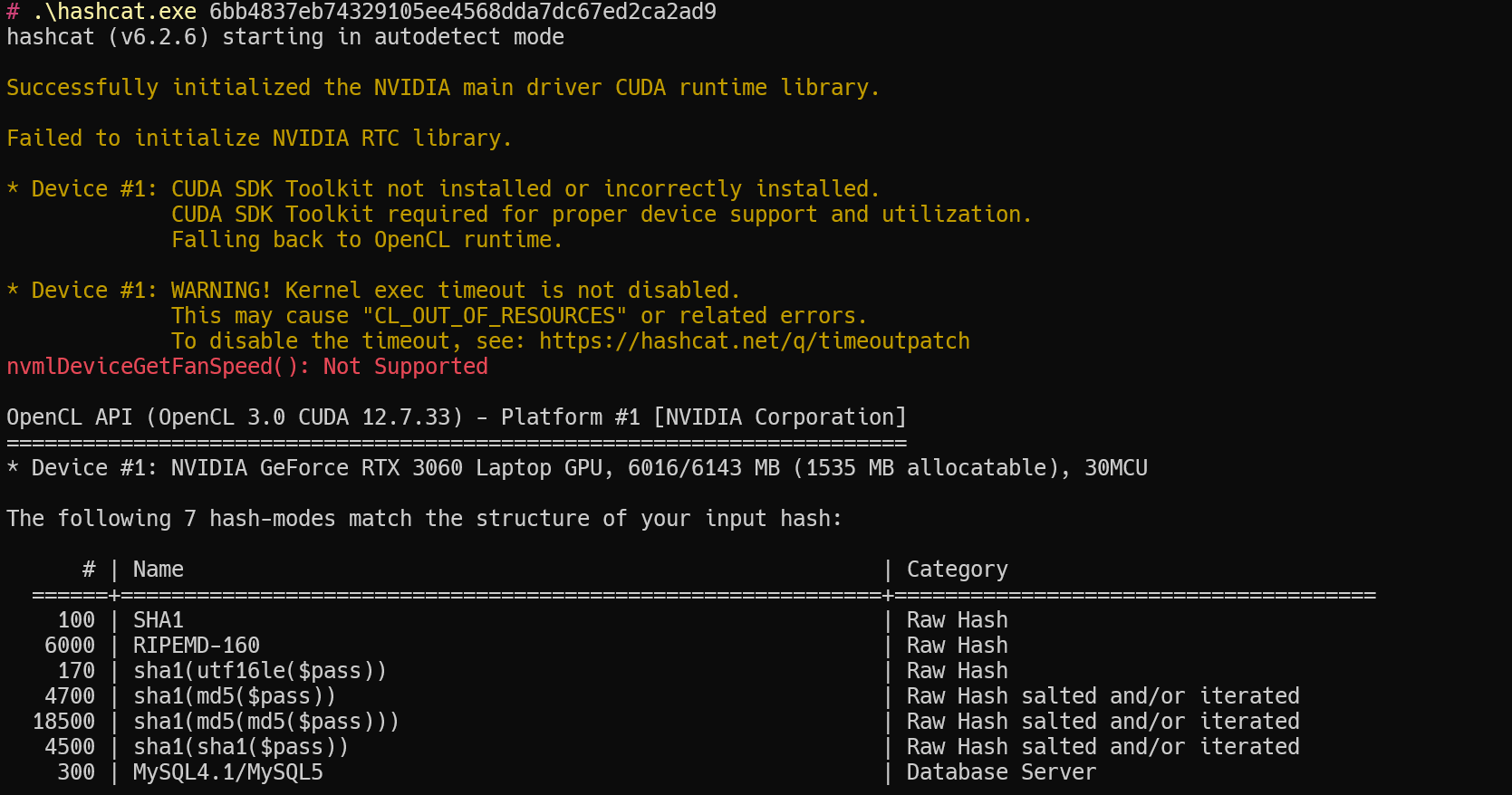
使用字典爆破MD5(也可以是多个md5)
1 | hashcat -a 0 -m 0 8914de686ab28dc22f30d3d8e107ff6c "E:\400W常用密码(整理).txt" |
将多个md5放在文件里
1 | hashcat -a 0 -m 0 hash.txt "E:\400W常用密码(整理).txt" |
使用掩码爆破MD5(也可以是多个md5)
规则请查看上文
1 | hashcat -a 3 -m 0 8914de686ab28dc22f30d3d8e107ff6c xxxxxxxxxx //x处为自己填写的掩码 |
将多个md5放在文件里
1 | hashcat -a 3 -m 0 hash.txt xxxxxxxxxx //x处为自己填写的掩码 |
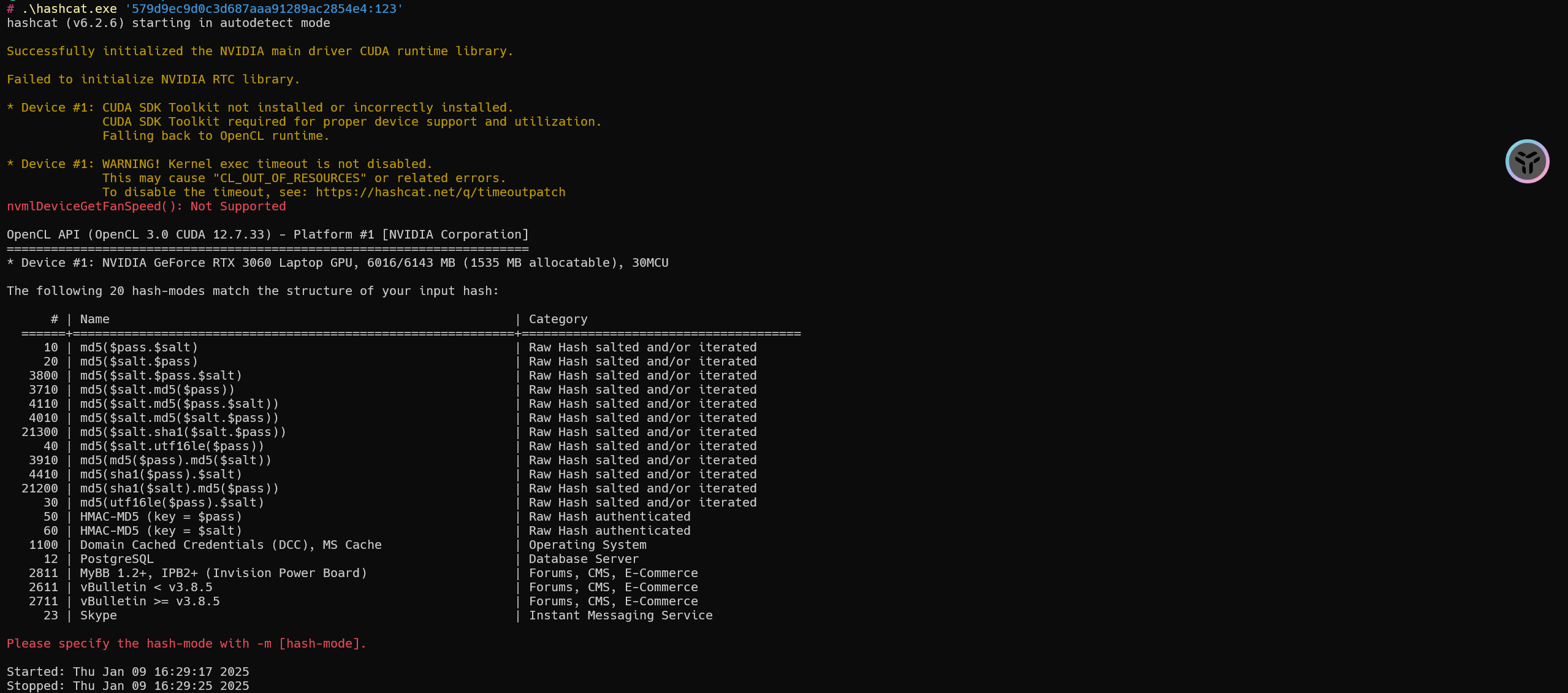
使用字典爆破加盐的MD5
值为
1 | 579d9ec9d0c3d687aaa91289ac2854e4:123 |
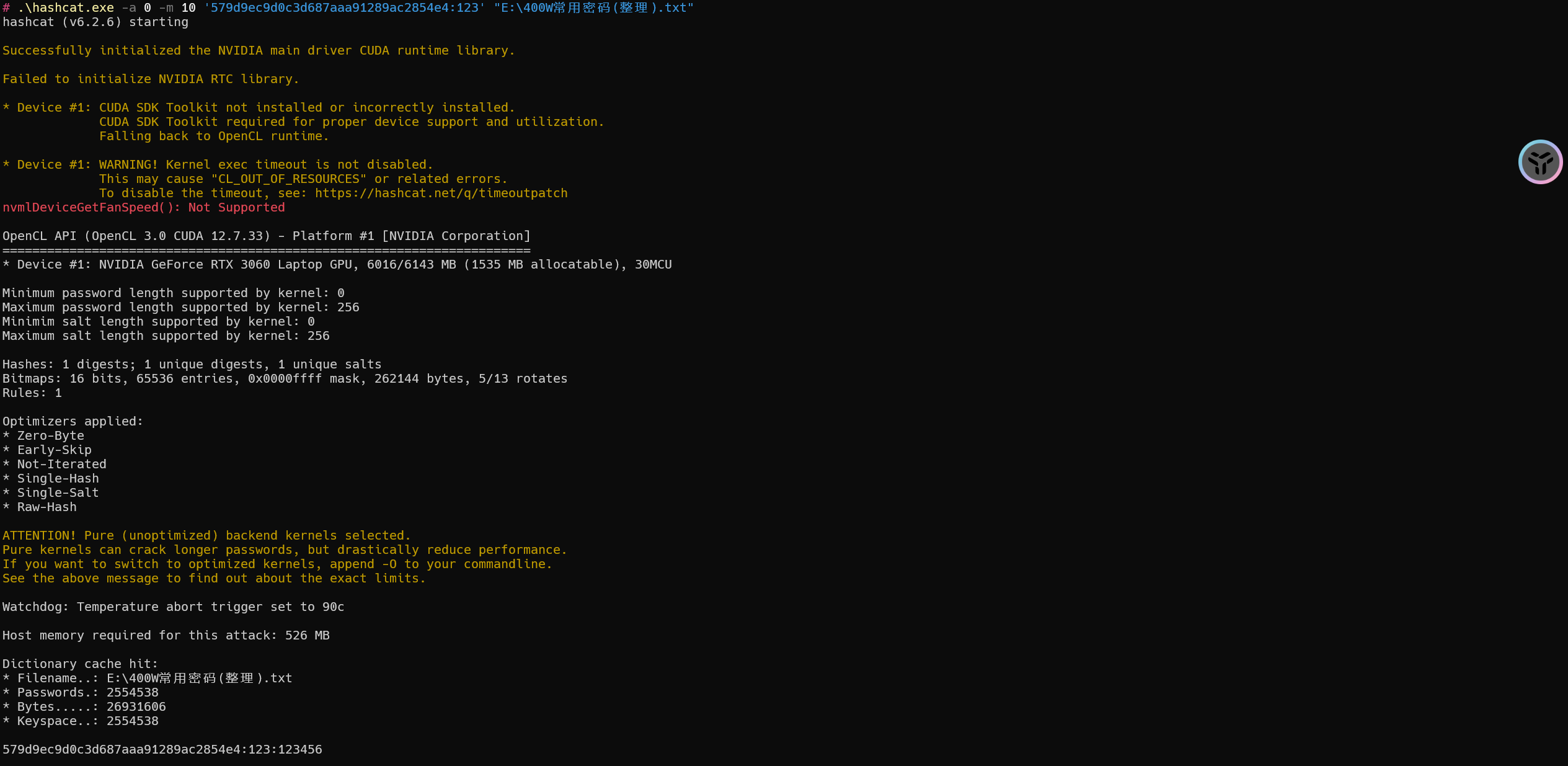
示例
1 | hashcat -a 0 -m 10 '579d9ec9d0c3d687aaa91289ac2854e4:123' "E:\400W常用密码(整理).txt" |
使用字典爆破Bcrypt
引号只是用来转义,同上文中的$
1 | hashcat -a 0 -m 3200 '$2a$09$PiCiFNspSlTBE9CakVs8ZOqx0xa03X9wOm01gMasHch4929TpEWCC' "E:\400W常用密码(整理).txt" |
也可破解多个,同上文中MD5破解
破解WIFI密码
首先要有握手包,并且新版的hashcat,已经不支持旧版的格式,需要使用hcxtools工具中的hcxpcapngtool将包转为hashcat支持的格式
也可以使用hashcat官方提供的网页转换工具hashcat hcxpcapngtool - advanced password recovery
示例
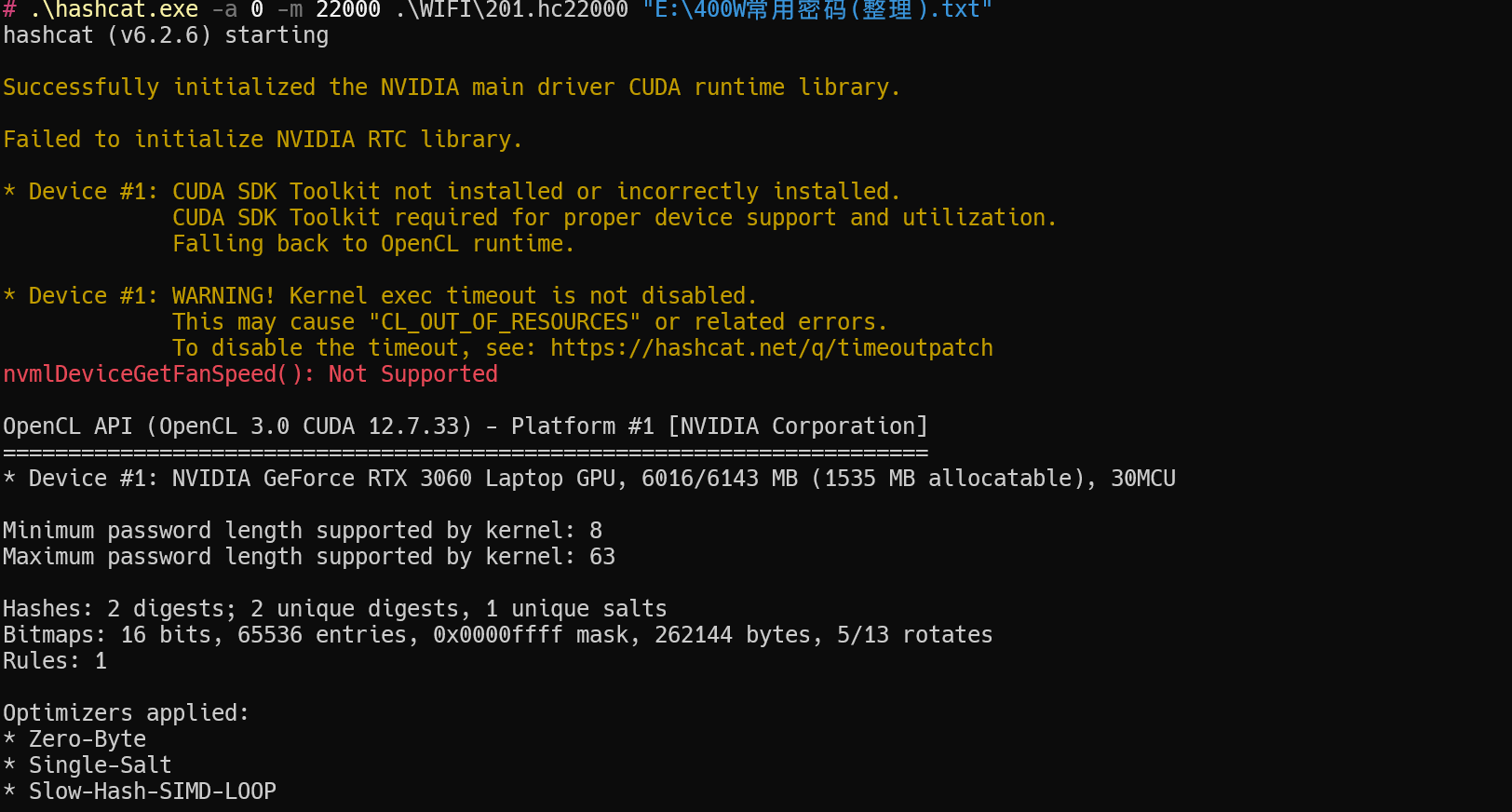
1 | hashcat -a 0 -m 22000 .\WIFI\201.hc22000 "E:\400W常用密码(整理).txt" |
破解MySQL数据库密码
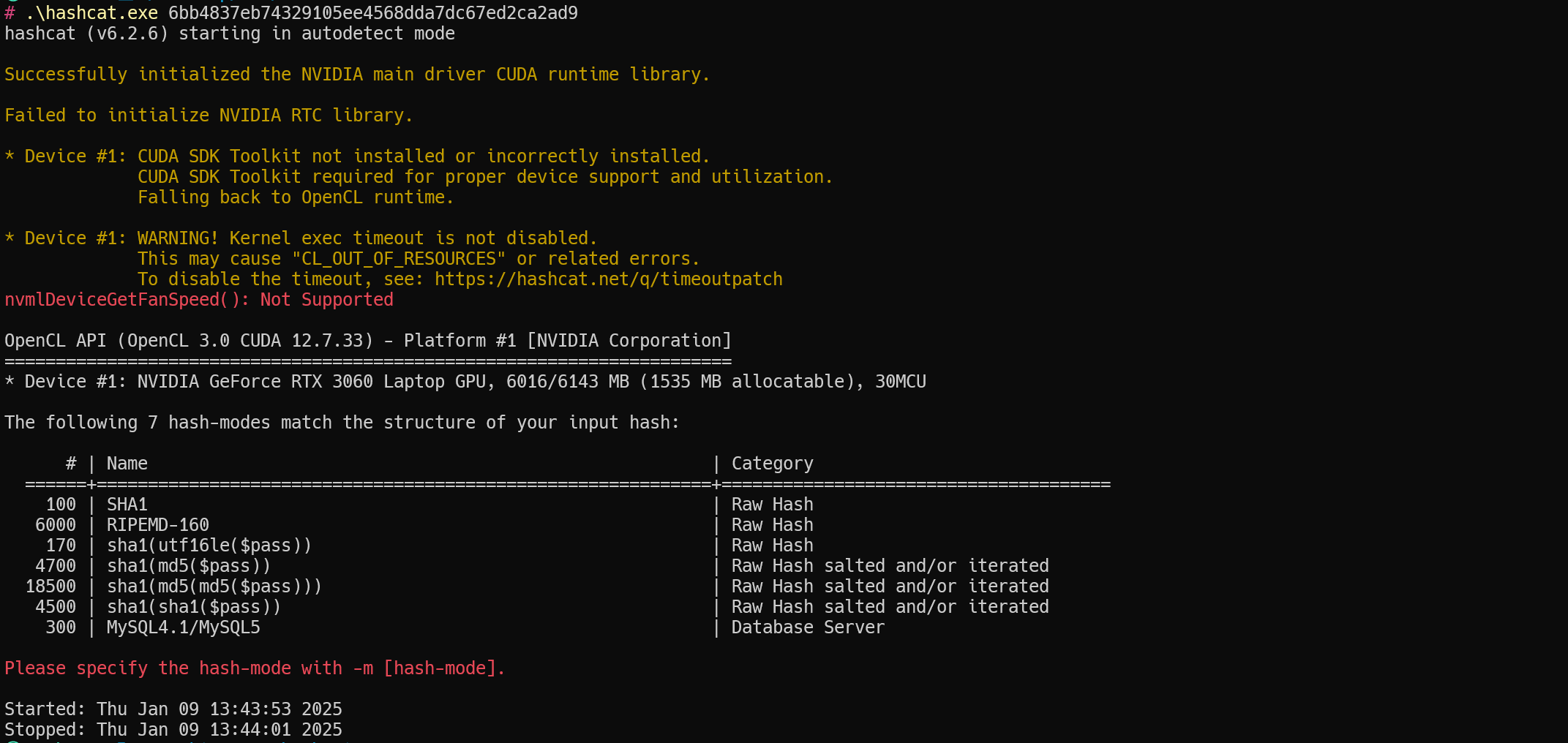
我临时加密了一个Mysql5的数据库密码
1 | hashcat -a 0 -m 300 6bb4837eb74329105ee4568dda7dc67ed2ca2ad9 "E:\400W常用密码(整理).txt" |
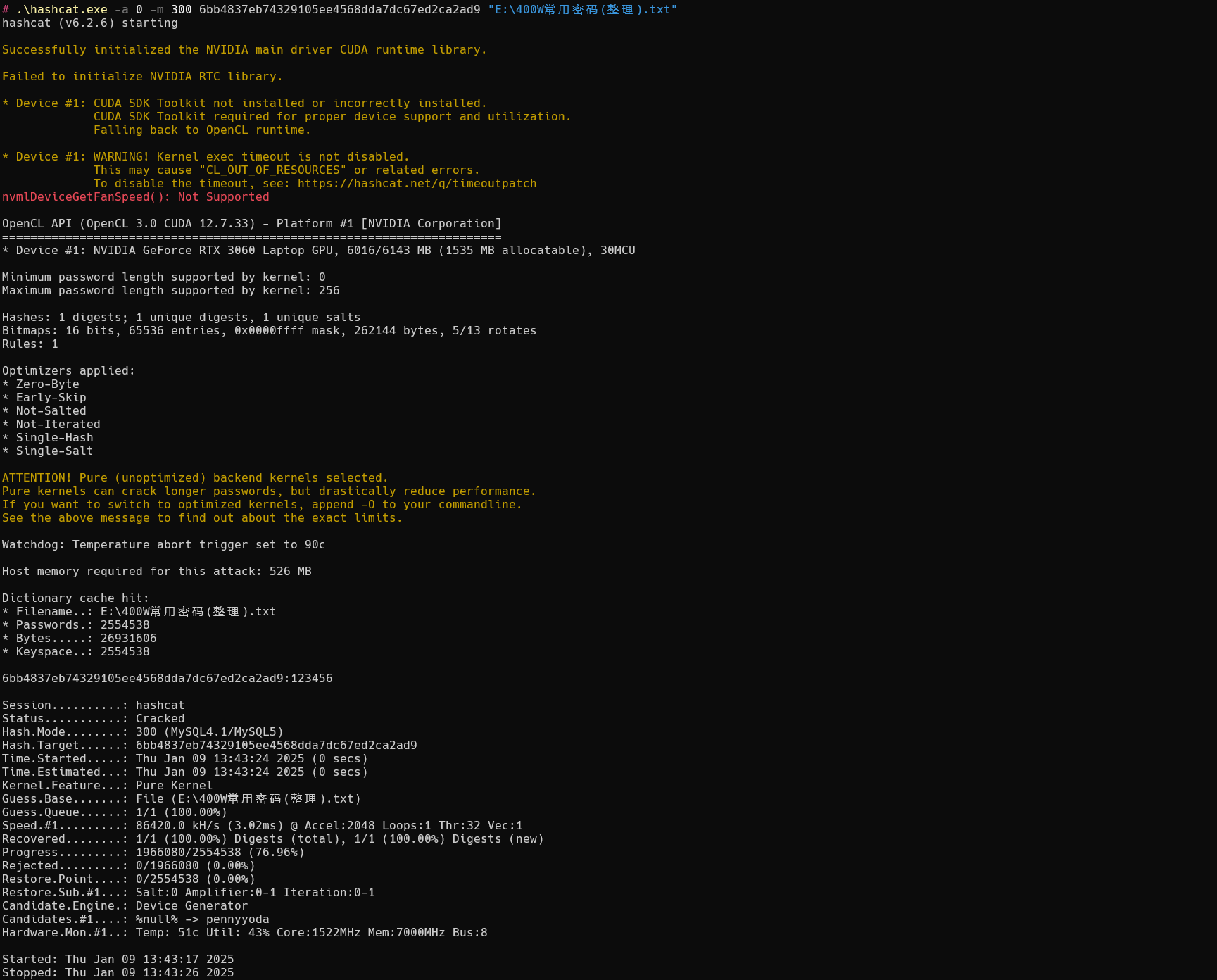
破解MSSQL
值为
1 | 0x010000000000a759cb9caac46bd28de0b3e2c382753deb0f83df |
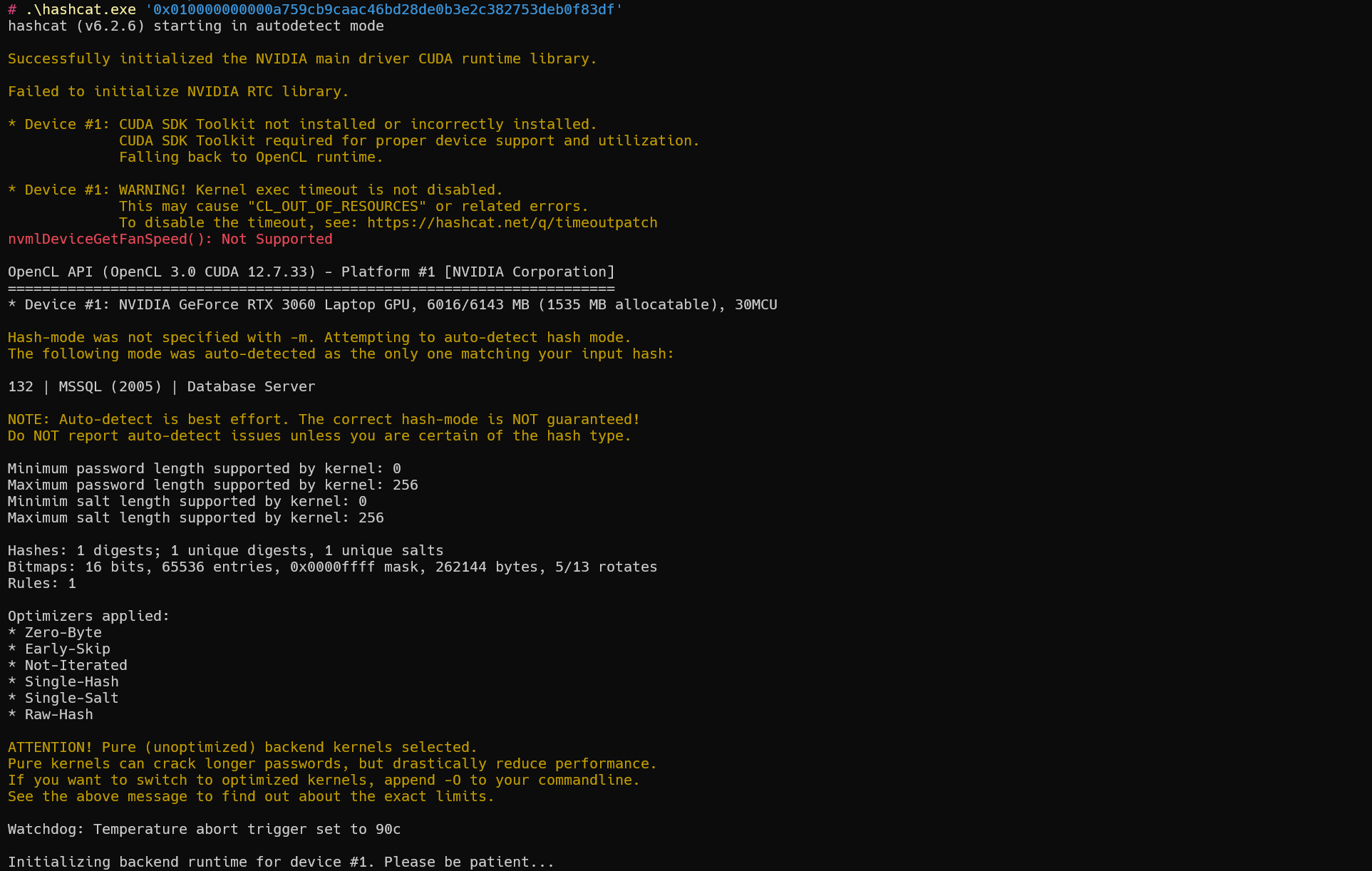
示例
1 | hashcat -a 0 -m 132 '0x010000000000a759cb9caac46bd28de0b3e2c382753deb0f83df' "E:\400W常用密码(整理).txt" |
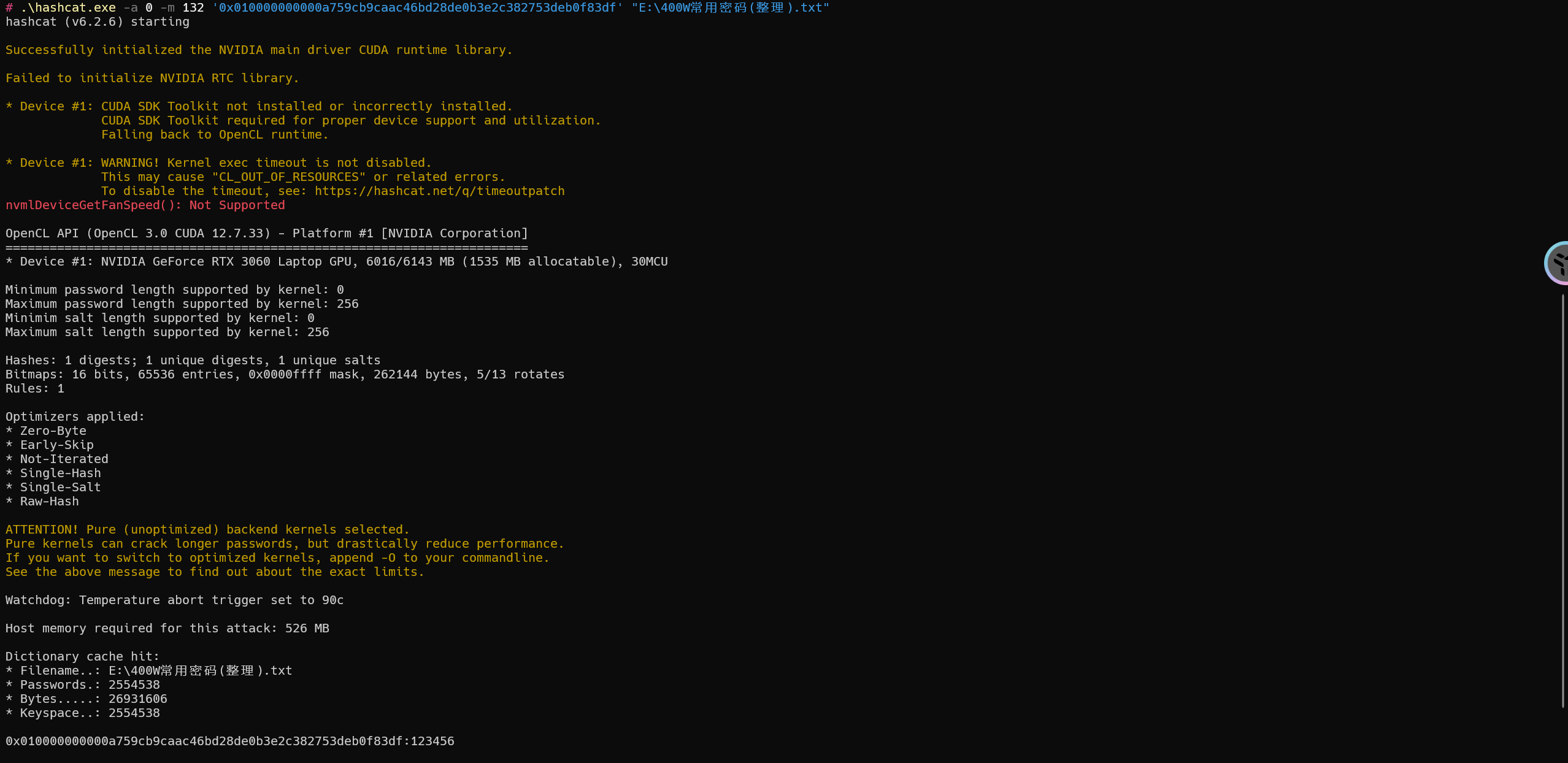
密码为:123456
破解压缩包密码
RAR
先使用John the Ripper获取hash值
1 | rar2john /home/kali/Desktop/1.rar |

值为
1 | $rar5$16$258426df09f80311004fd5c06094f883$15$614487d8b960e25811590fc850e42e9b$8$41e1d1a01de9bc64 |
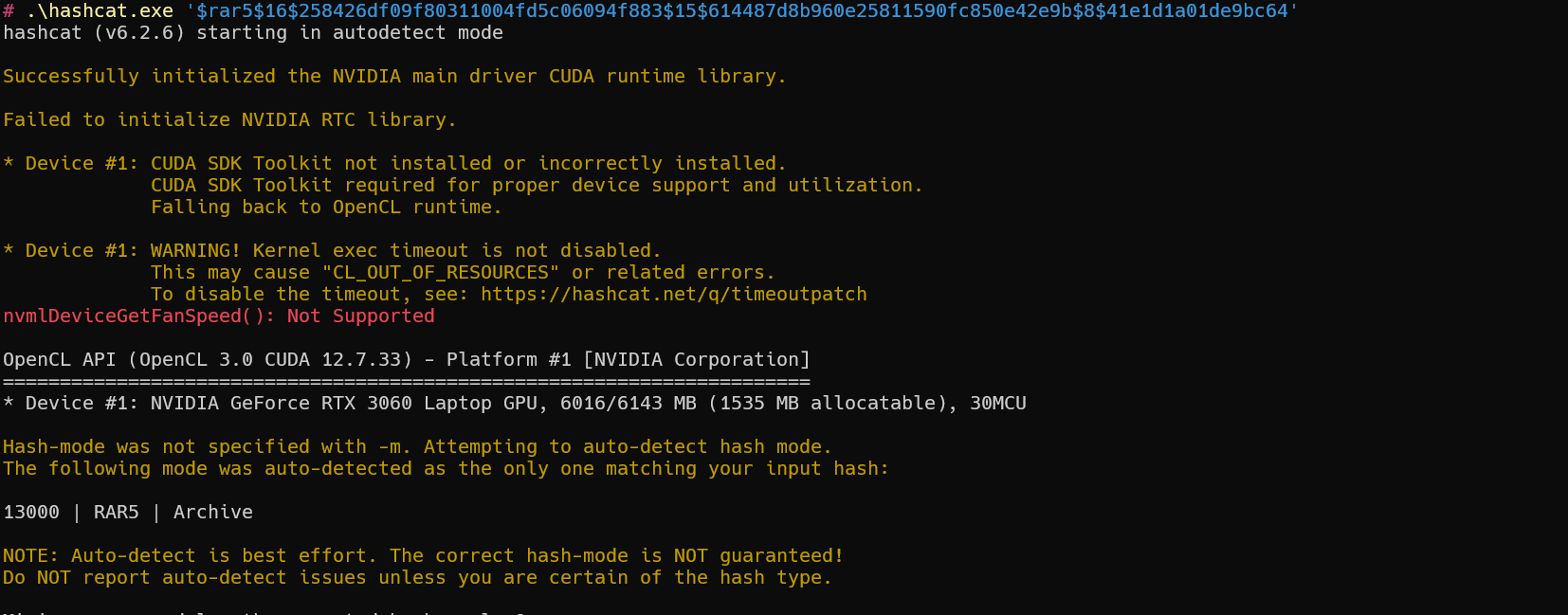
只有一个(Windows运行的话,建议把值放在文件里)
1 | hashcat -a 0 -m 13000 .\WIFI\rar.txt "E:\400W常用密码(整理).txt" |
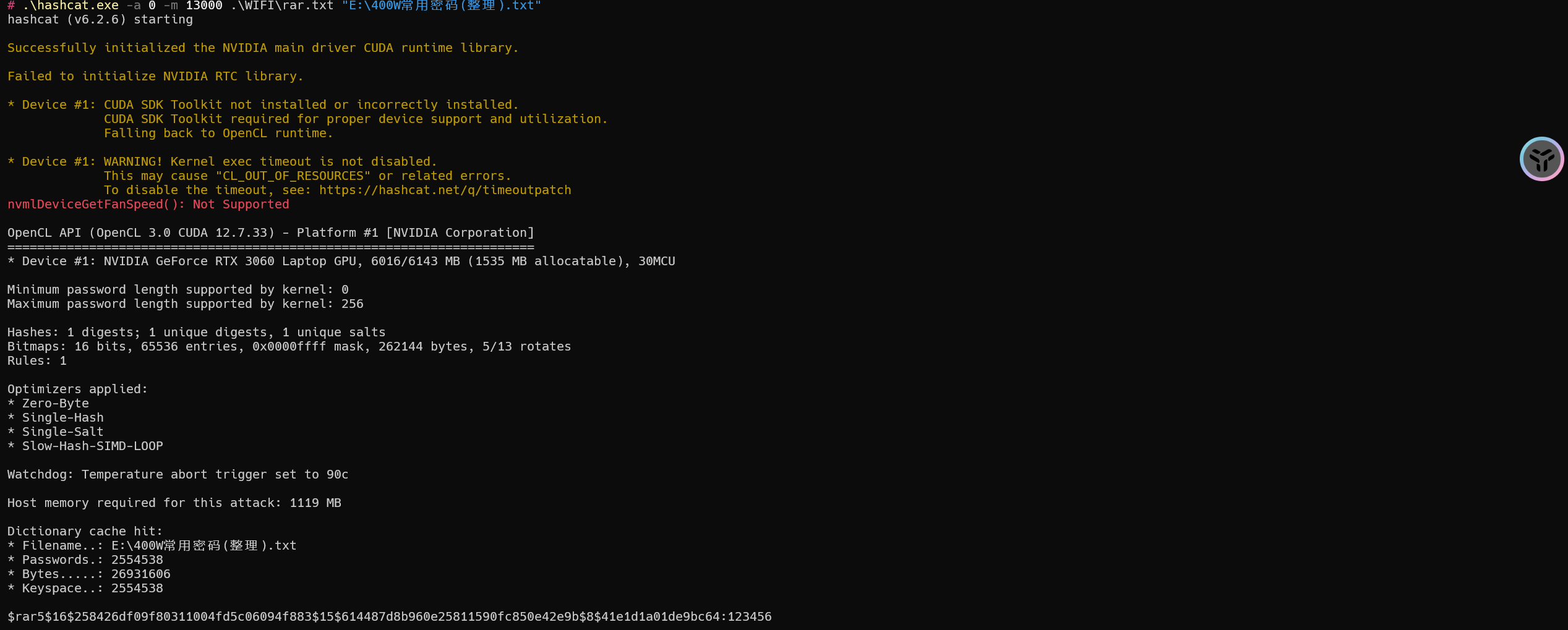
密码为:123456
ZIP
先使用John the Ripper获取hash值
1 | zip2john /home/kali/Desktop/test.zip |
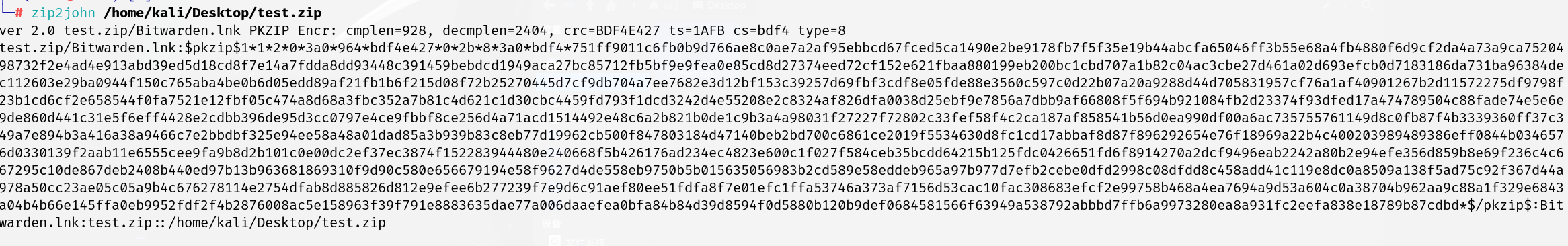
获取的值要去掉路径
1 | $pkzip$1*1*2*0*3a0*964*bdf4e427*0*2b*8*3a0*bdf4*751ff9011c6fb0b9d766ae8c0ae7a2af95ebbcd67fced5ca1490e2be9178fb7f5f35e19b44abcfa65046ff3b55e68a4fb4880f6d9cf2da4a73a9ca7520498732f2e4ad4e913abd39ed5d18cd8f7e14a7fdda8dd93448c391459bebdcd1949aca27bc85712fb5bf9e9fea0e85cd8d27374eed72cf152e621fbaa880199eb200bc1cbd707a1b82c04ac3cbe27d461a02d693efcb0d7183186da731ba96384dec112603e29ba0944f150c765aba4be0b6d05edd89af21fb1b6f215d08f72b25270445d7cf9db704a7ee7682e3d12bf153c39257d69fbf3cdf8e05fde88e3560c597c0d22b07a20a9288d44d705831957cf76a1af40901267b2d11572275df9798f23b1cd6cf2e658544f0fa7521e12fbf05c474a8d68a3fbc352a7b81c4d621c1d30cbc4459fd793f1dcd3242d4e55208e2c8324af826dfa0038d25ebf9e7856a7dbb9af66808f5f694b921084fb2d23374f93dfed17a474789504c88fade74e5e6e9de860d441c31e5f6eff4428e2cdbb396de95d3cc0797e4ce9fbbf8ce256d4a71acd1514492e48c6a2b821b0de1c9b3a4a98031f27227f72802c33fef58f4c2ca187af858541b56d0ea990df00a6ac735755761149d8c0fb87f4b3339360ff37c349a7e894b3a416a38a9466c7e2bbdbf325e94ee58a48a01dad85a3b939b83c8eb77d19962cb500f847803184d47140beb2bd700c6861ce2019f5534630d8fc1cd17abbaf8d87f896292654e76f18969a22b4c400203989489386eff0844b0346576d0330139f2aab11e6555cee9fa9b8d2b101c0e00dc2ef37ec3874f152283944480e240668f5b426176ad234ec4823e600c1f027f584ceb35bcdd64215b125fdc0426651fd6f8914270a2dcf9496eab2242a80b2e94efe356d859b8e69f236c4c667295c10de867deb2408b440ed97b13b963681869310f9d90c580e656679194e58f9627d4de558eb9750b5b015635056983b2cd589e58eddeb965a97b977d7efb2cebe0dfd2998c08dfdd8c458add41c119e8dc0a8509a138f5ad75c92f367d44a978a50cc23ae05c05a9b4c676278114e2754dfab8d885826d812e9efee6b277239f7e9d6c91aef80ee51fdfa8f7e01efc1ffa53746a373af7156d53cac10fac308683efcf2e99758b468a4ea7694a9d53a604c0a38704b962aa9c88a1f329e6843a04b4b66e145ffa0eb9952fdf2f4b2876008ac5e158963f39f791e8883635dae77a006daaefea0bfa84b84d39d8594f0d5880b120b9def0684581566f63949a538792abbbd7ffb6a9973280ea8a931fc2eefa838e18789b87cdbd*$/pkzip$ |
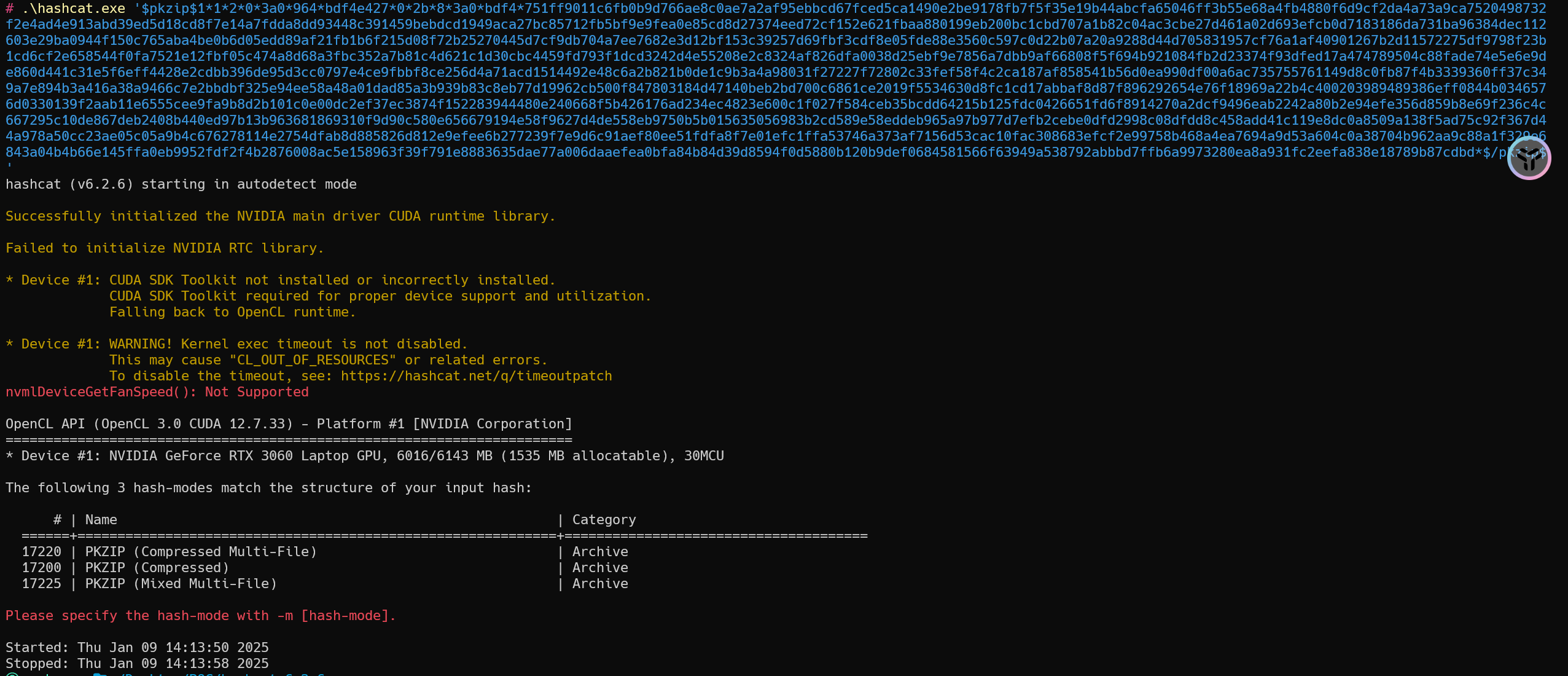
识别出三种模式,可以一个个试
1 | hashcat -a 0 -m 17220 '$pkzip$1*1*2*0*3a0*964*bdf4e427*0*2b*8*3a0*bdf4*751ff9011c6fb0b9d766ae8c0ae7a2af95ebbcd67fced5ca1490e2be9178fb7f5f35e19b44abcfa65046ff3b55e68a4fb4880f6d9cf2da4a73a9ca7520498732f2e4ad4e913abd39ed5d18cd8f7e14a7fdda8dd93448c391459bebdcd1949aca27bc85712fb5bf9e9fea0e85cd8d27374eed72cf152e621fbaa880199eb200bc1cbd707a1b82c04ac3cbe27d461a02d693efcb0d7183186da731ba96384dec112603e29ba0944f150c765aba4be0b6d05edd89af21fb1b6f215d08f72b25270445d7cf9db704a7ee7682e3d12bf153c39257d69fbf3cdf8e05fde88e3560c597c0d22b07a20a9288d44d705831957cf76a1af40901267b2d11572275df9798f23b1cd6cf2e658544f0fa7521e12fbf05c474a8d68a3fbc352a7b81c4d621c1d30cbc4459fd793f1dcd3242d4e55208e2c8324af826dfa0038d25ebf9e7856a7dbb9af66808f5f694b921084fb2d23374f93dfed17a474789504c88fade74e5e6e9de860d441c31e5f6eff4428e2cdbb396de95d3cc0797e4ce9fbbf8ce256d4a71acd1514492e48c6a2b821b0de1c9b3a4a98031f27227f72802c33fef58f4c2ca187af858541b56d0ea990df00a6ac735755761149d8c0fb87f4b3339360ff37c349a7e894b3a416a38a9466c7e2bbdbf325e94ee58a48a01dad85a3b939b83c8eb77d19962cb500f847803184d47140beb2bd700c6861ce2019f5534630d8fc1cd17abbaf8d87f896292654e76f18969a22b4c400203989489386eff0844b0346576d0330139f2aab11e6555cee9fa9b8d2b101c0e00dc2ef37ec3874f152283944480e240668f5b426176ad234ec4823e600c1f027f584ceb35bcdd64215b125fdc0426651fd6f8914270a2dcf9496eab2242a80b2e94efe356d859b8e69f236c4c667295c10de867deb2408b440ed97b13b963681869310f9d90c580e656679194e58f9627d4de558eb9750b5b015635056983b2cd589e58eddeb965a97b977d7efb2cebe0dfd2998c08dfdd8c458add41c119e8dc0a8509a138f5ad75c92f367d44a978a50cc23ae05c05a9b4c676278114e2754dfab8d885826d812e9efee6b277239f7e9d6c91aef80ee51fdfa8f7e01efc1ffa53746a373af7156d53cac10fac308683efcf2e99758b468a4ea7694a9d53a604c0a38704b962aa9c88a1f329e6843a04b4b66e145ffa0eb9952fdf2f4b2876008ac5e158963f39f791e8883635dae77a006daaefea0bfa84b84d39d8594f0d5880b120b9def0684581566f63949a538792abbbd7ffb6a9973280ea8a931fc2eefa838e18789b87cdbd*$/pkzip$' "E:\400W常用密码(整理).txt" |
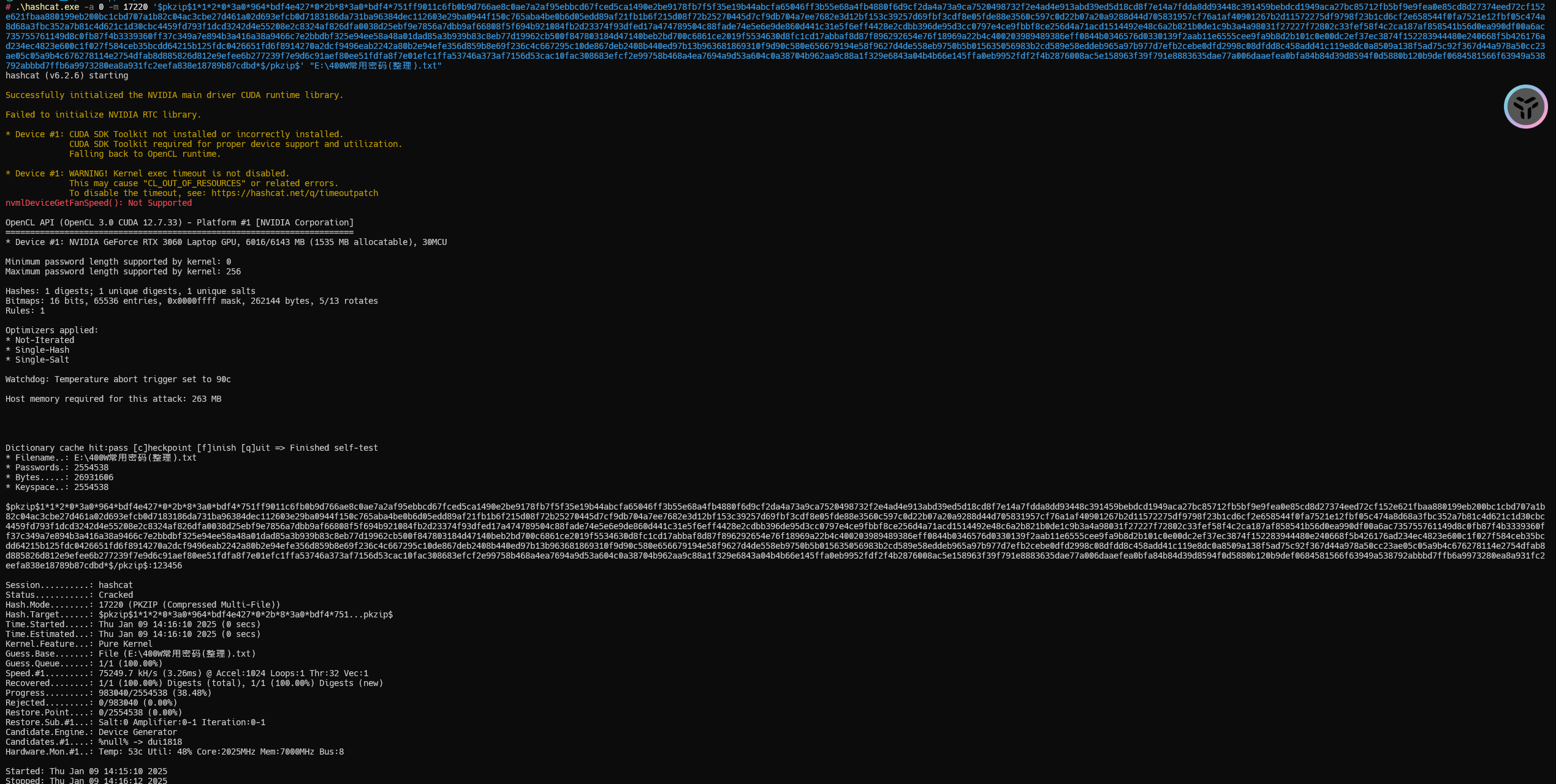
破解成功密码是:123456
7-zip
先使用John the Ripper获取hash值
1 | 7z2john /home/kali/Desktop/test.7z |
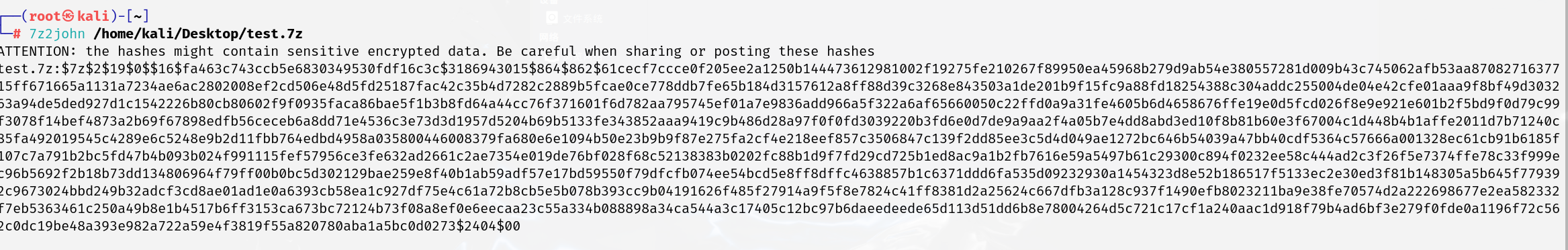
值为
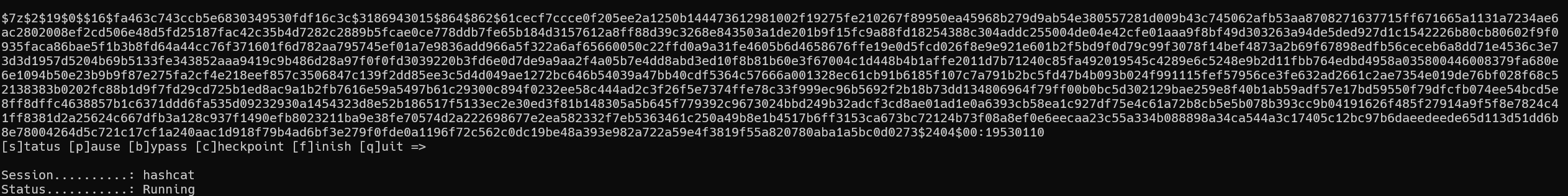
1 | $7z$2$19$0$$16$fa463c743ccb5e6830349530fdf16c3c$3186943015$864$862$61cecf7ccce0f205ee2a1250b144473612981002f19275fe210267f89950ea45968b279d9ab54e380557281d009b43c745062afb53aa8708271637715ff671665a1131a7234ae6ac2802008ef2cd506e48d5fd25187fac42c35b4d7282c2889b5fcae0ce778ddb7fe65b184d3157612a8ff88d39c3268e843503a1de201b9f15fc9a88fd18254388c304addc255004de04e42cfe01aaa9f8bf49d303263a94de5ded927d1c1542226b80cb80602f9f0935faca86bae5f1b3b8fd64a44cc76f371601f6d782aa795745ef01a7e9836add966a5f322a6af65660050c22ffd0a9a31fe4605b6d4658676ffe19e0d5fcd026f8e9e921e601b2f5bd9f0d79c99f3078f14bef4873a2b69f67898edfb56ceceb6a8dd71e4536c3e73d3d1957d5204b69b5133fe343852aaa9419c9b486d28a97f0f0fd3039220b3fd6e0d7de9a9aa2f4a05b7e4dd8abd3ed10f8b81b60e3f67004c1d448b4b1affe2011d7b71240c85fa492019545c4289e6c5248e9b2d11fbb764edbd4958a035800446008379fa680e6e1094b50e23b9b9f87e275fa2cf4e218eef857c3506847c139f2dd85ee3c5d4d049ae1272bc646b54039a47bb40cdf5364c57666a001328ec61cb91b6185f107c7a791b2bc5fd47b4b093b024f991115fef57956ce3fe632ad2661c2ae7354e019de76bf028f68c52138383b0202fc88b1d9f7fd29cd725b1ed8ac9a1b2fb7616e59a5497b61c29300c894f0232ee58c444ad2c3f26f5e7374ffe78c33f999ec96b5692f2b18b73dd134806964f79ff00b0bc5d302129bae259e8f40b1ab59adf57e17bd59550f79dfcfb074ee54bcd5e8ff8dffc4638857b1c6371ddd6fa535d09232930a1454323d8e52b186517f5133ec2e30ed3f81b148305a5b645f779392c9673024bbd249b32adcf3cd8ae01ad1e0a6393cb58ea1c927df75e4c61a72b8cb5e5b078b393cc9b04191626f485f27914a9f5f8e7824c41ff8381d2a25624c667dfb3a128c937f1490efb8023211ba9e38fe70574d2a222698677e2ea582332f7eb5363461c250a49b8e1b4517b6ff3153ca673bc72124b73f08a8ef0e6eecaa23c55a334b088898a34ca544a3c17405c12bc97b6daeedeede65d113d51dd6b8e78004264d5c721c17cf1a240aac1d918f79b4ad6bf3e279f0fde0a1196f72c562c0dc19be48a393e982a722a59e4f3819f55a820780aba1a5bc0d0273$2404$00 |
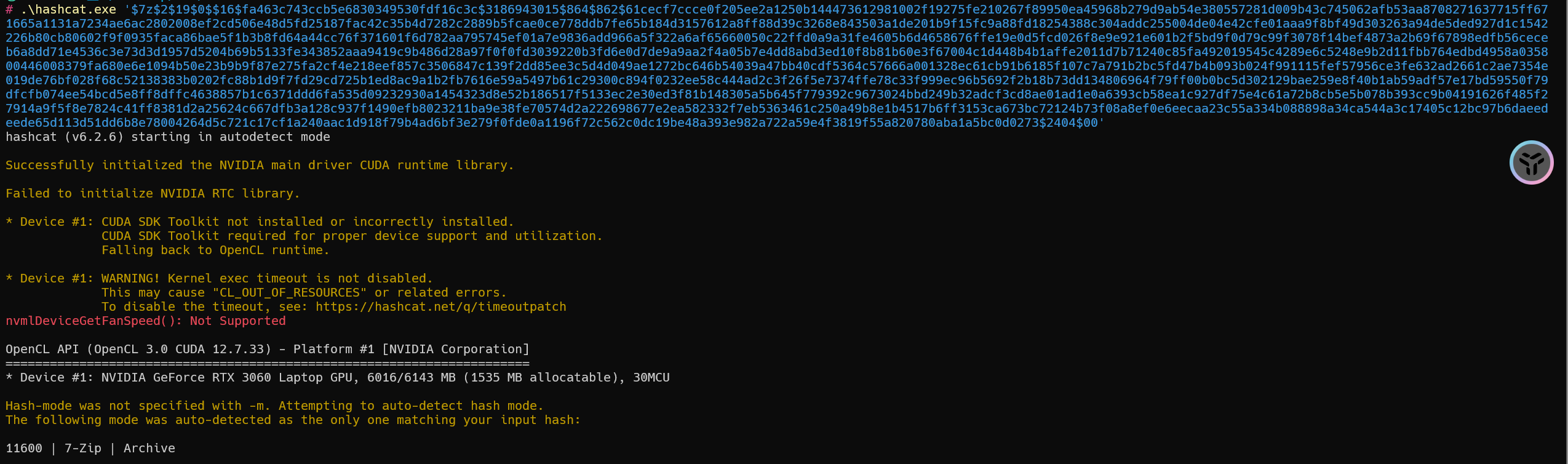
还有一句提示,一个hash对应多个密码,加上--keep-guessing破解出第一个继续破解
只有一个
1 | hashcat -a 0 -m 11600 '$7z$2$19$0$$16$fa463c743ccb5e6830349530fdf16c3c$3186943015$864$862$61cecf7ccce0f205ee2a1250b144473612981002f19275fe210267f89950ea45968b279d9ab54e380557281d009b43c745062afb53aa8708271637715ff671665a1131a7234ae6ac2802008ef2cd506e48d5fd25187fac42c35b4d7282c2889b5fcae0ce778ddb7fe65b184d3157612a8ff88d39c3268e843503a1de201b9f15fc9a88fd18254388c304addc255004de04e42cfe01aaa9f8bf49d303263a94de5ded927d1c1542226b80cb80602f9f0935faca86bae5f1b3b8fd64a44cc76f371601f6d782aa795745ef01a7e9836add966a5f322a6af65660050c22ffd0a9a31fe4605b6d4658676ffe19e0d5fcd026f8e9e921e601b2f5bd9f0d79c99f3078f14bef4873a2b69f67898edfb56ceceb6a8dd71e4536c3e73d3d1957d5204b69b5133fe343852aaa9419c9b486d28a97f0f0fd3039220b3fd6e0d7de9a9aa2f4a05b7e4dd8abd3ed10f8b81b60e3f67004c1d448b4b1affe2011d7b71240c85fa492019545c4289e6c5248e9b2d11fbb764edbd4958a035800446008379fa680e6e1094b50e23b9b9f87e275fa2cf4e218eef857c3506847c139f2dd85ee3c5d4d049ae1272bc646b54039a47bb40cdf5364c57666a001328ec61cb91b6185f107c7a791b2bc5fd47b4b093b024f991115fef57956ce3fe632ad2661c2ae7354e019de76bf028f68c52138383b0202fc88b1d9f7fd29cd725b1ed8ac9a1b2fb7616e59a5497b61c29300c894f0232ee58c444ad2c3f26f5e7374ffe78c33f999ec96b5692f2b18b73dd134806964f79ff00b0bc5d302129bae259e8f40b1ab59adf57e17bd59550f79dfcfb074ee54bcd5e8ff8dffc4638857b1c6371ddd6fa535d09232930a1454323d8e52b186517f5133ec2e30ed3f81b148305a5b645f779392c9673024bbd249b32adcf3cd8ae01ad1e0a6393cb58ea1c927df75e4c61a72b8cb5e5b078b393cc9b04191626f485f27914a9f5f8e7824c41ff8381d2a25624c667dfb3a128c937f1490efb8023211ba9e38fe70574d2a222698677e2ea582332f7eb5363461c250a49b8e1b4517b6ff3153ca673bc72124b73f08a8ef0e6eecaa23c55a334b088898a34ca544a3c17405c12bc97b6daeedeede65d113d51dd6b8e78004264d5c721c17cf1a240aac1d918f79b4ad6bf3e279f0fde0a1196f72c562c0dc19be48a393e982a722a59e4f3819f55a820780aba1a5bc0d0273$2404$00' "E:\400W常用密码(整理).txt" --keep-guessing |
加上--keep-guessing是因为有时候第一个破解出的密码并不一定是真实密码
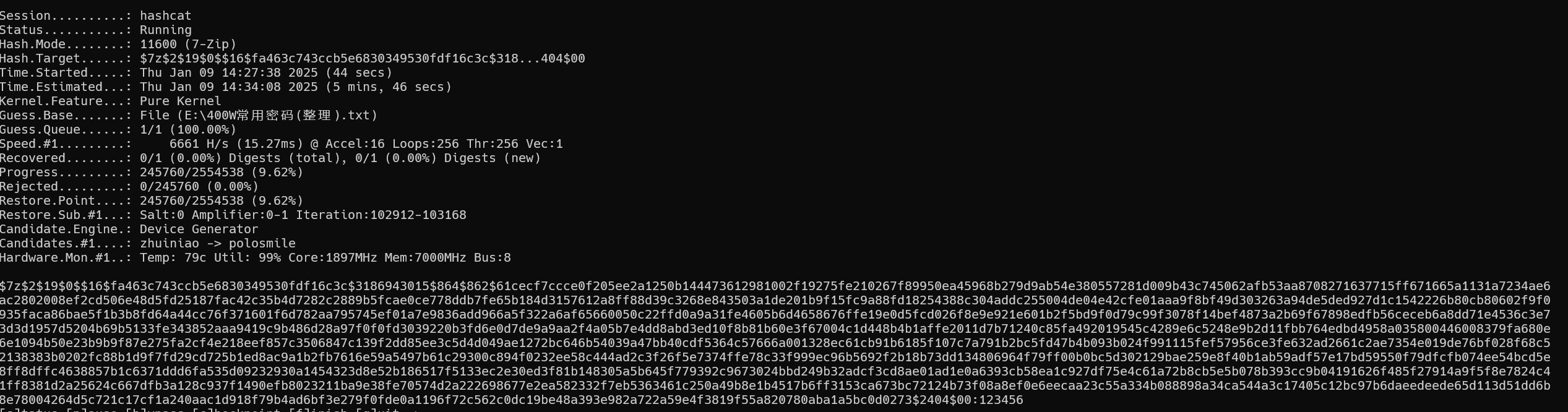
密码其实是:123456
破解Linux密码
在/etc/shadow文件中
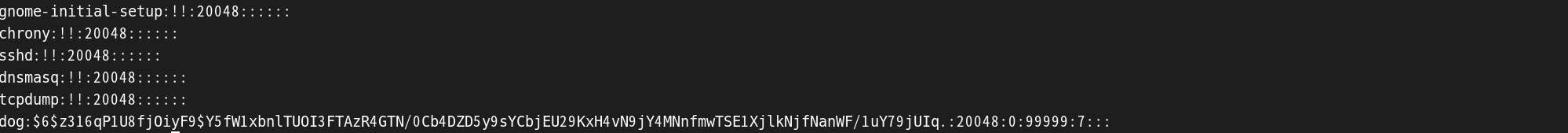
值为(.不要忘了)
1 | $6$z316qP1U8fjOiyF9$Y5fW1xbnlTUOI3FTAzR4GTN/0Cb4DZD5y9sYCbjEU29KxH4vN9jY4MNnfmwTSE1XjlkNjfNanWF/1uY79jUIq. |
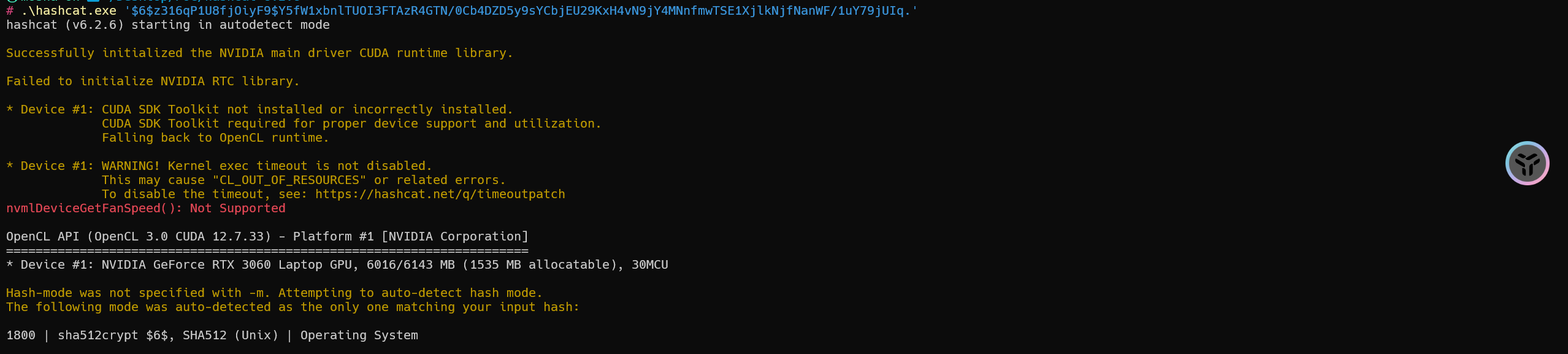
格式
1 | 用户名(username):加密后的密码($type$salt$encrypted):最后一次修改密码的日期(比如19429):最小修改密码间隔(0):最大修改密码间隔(99999):密码过期前的警告天数(7):密码过期后的宽限天数():账户失效日期():保留字段() |
$type
1 | 1 代表采用了MD5加密方式 |
示例
1 | hashcat.exe -a 0 -m 1800 '$6$z316qP1U8fjOiyF9$Y5fW1xbnlTUOI3FTAzR4GTN/0Cb4DZD5y9sYCbjEU29KxH4vN9jY4MNnfmwTSE1XjlkNjfNanWF/1uY79jUIq.' "E:\400W常用密码(整理).txt" |
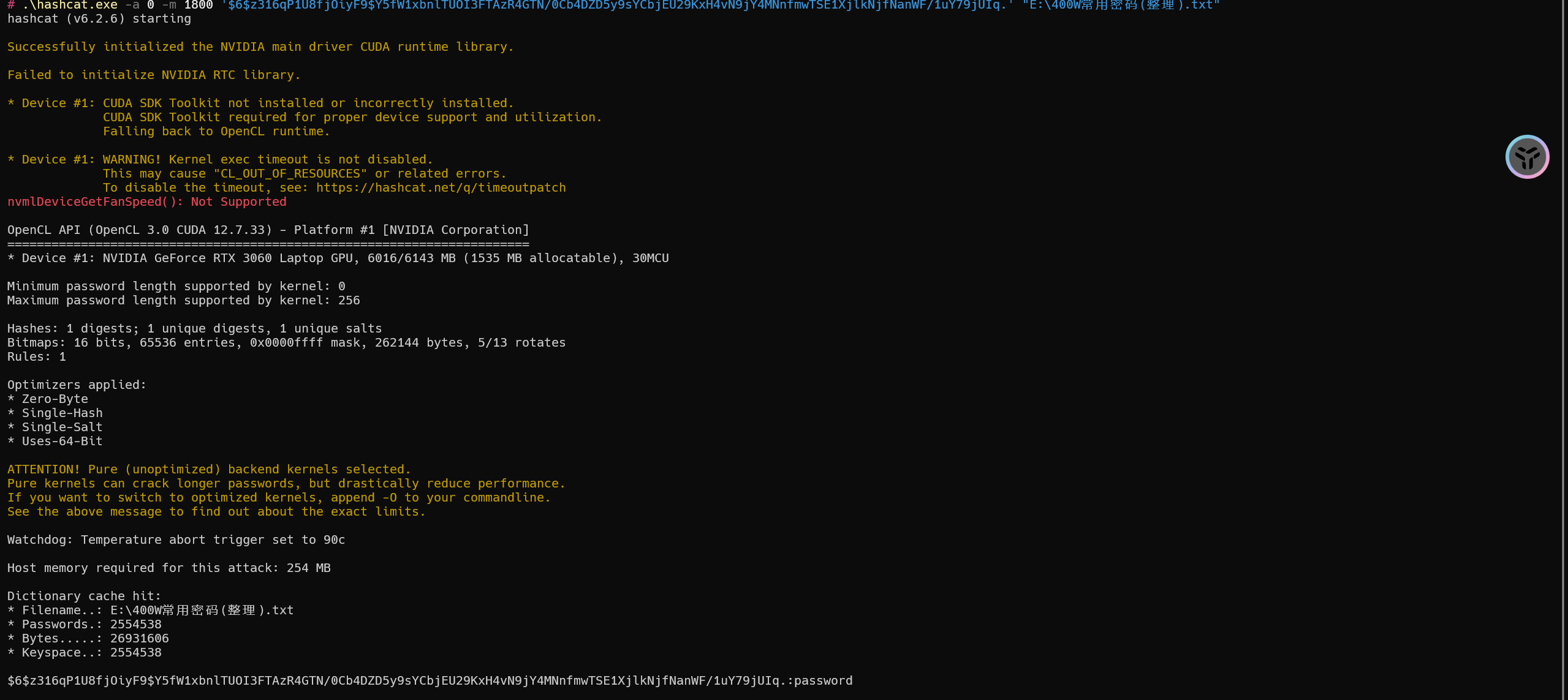
密码为:password
破解Windows密码
NTLM—HASH
正常情况需要用猕猴桃获取hash
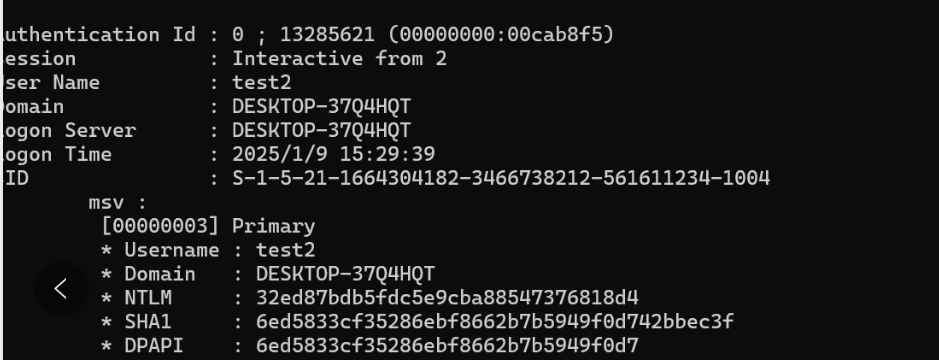
我们这里就不使用了,我们使用在线生成NTLM哈希 - 工具匠
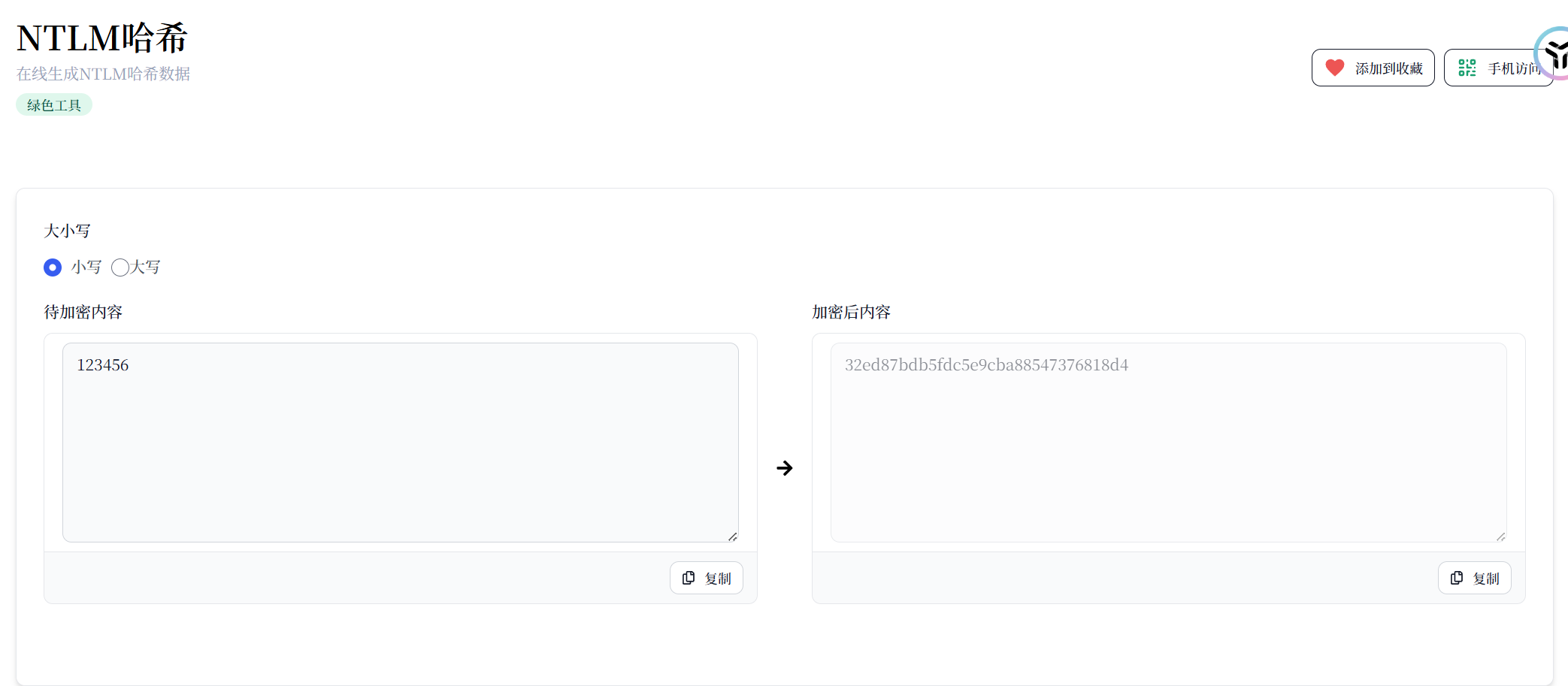
值为
1 | 32ed87bdb5fdc5e9cba88547376818d4 |
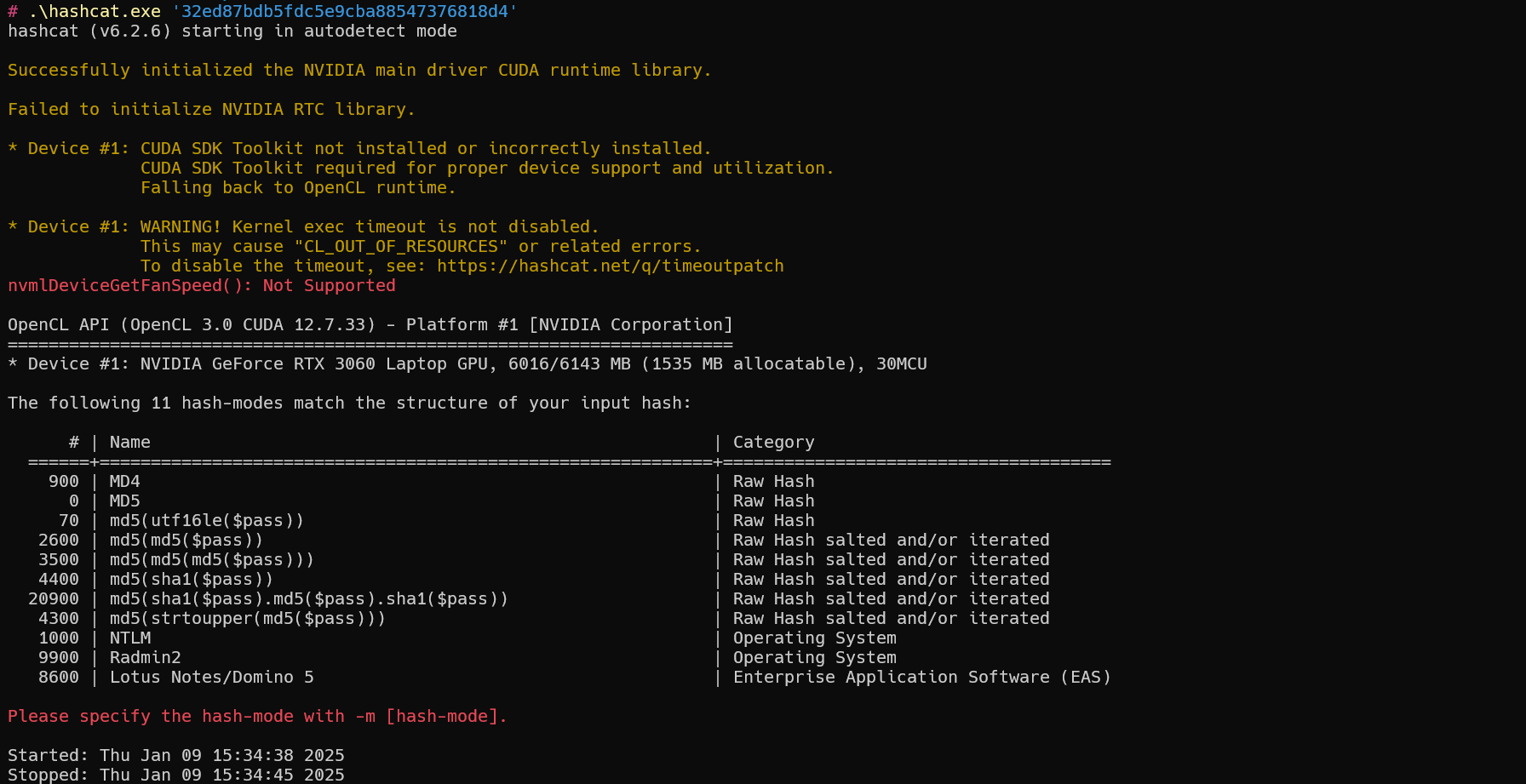
示例
1 | hashcat -a 0 -m 1000 '32ed87bdb5fdc5e9cba88547376818d4' "E:\400W常用密码(整理).txt" |
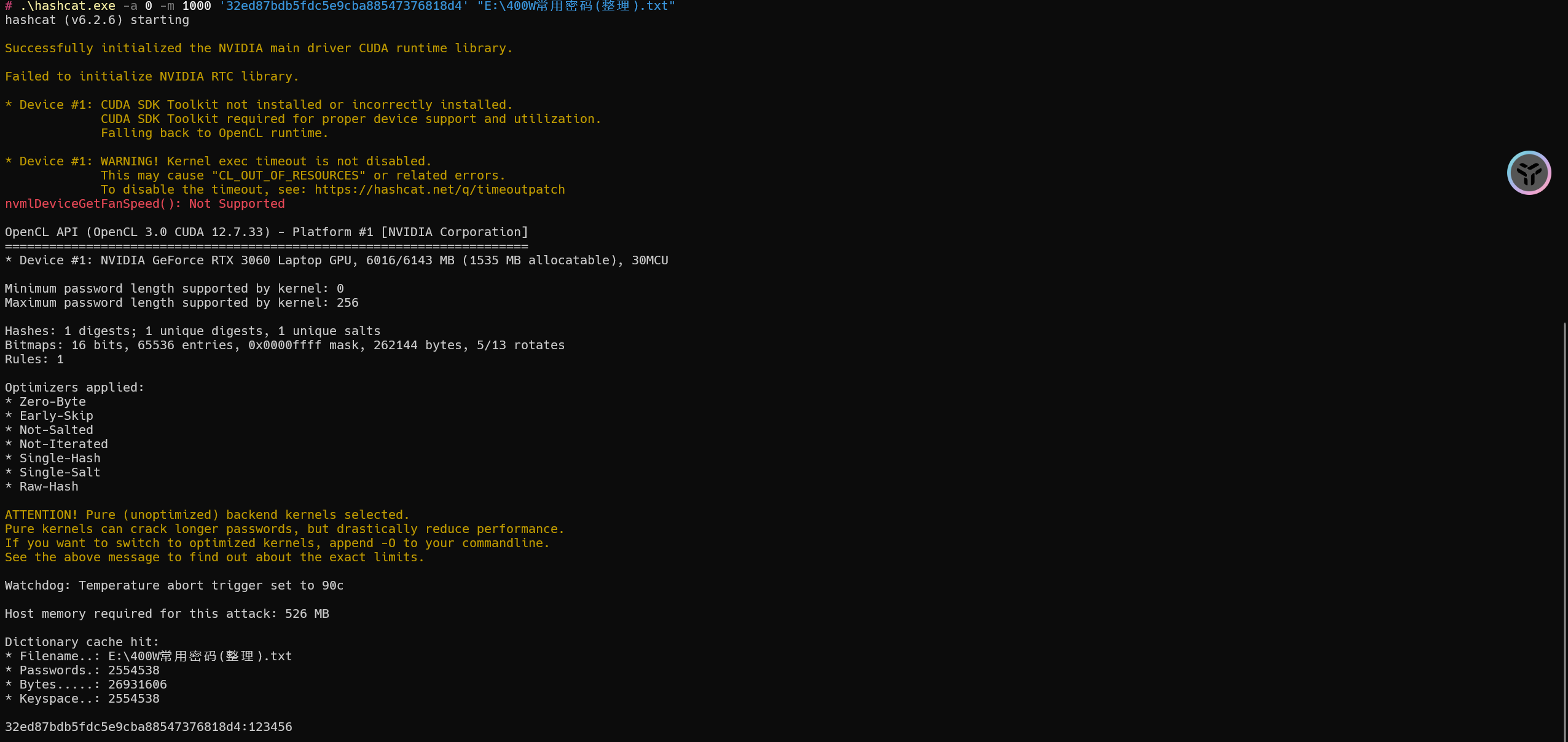
密码为:123456
LM-HASH
这里正常也需要猕猴桃获取,为了方便我这里就直接生成了
LM Hash
- 密码最多14个字符,超过部分被截断。
- 所有字母被转换为大写。
- 如果密码不足14个字符,用空字符(0x00)填充。
- 生成为一个32位的hash,前16位代表这前7个字符,后16位代表后7个字符
- 如果后16位固定位
aad3b435b51404ee那么密码小于等于7个字符
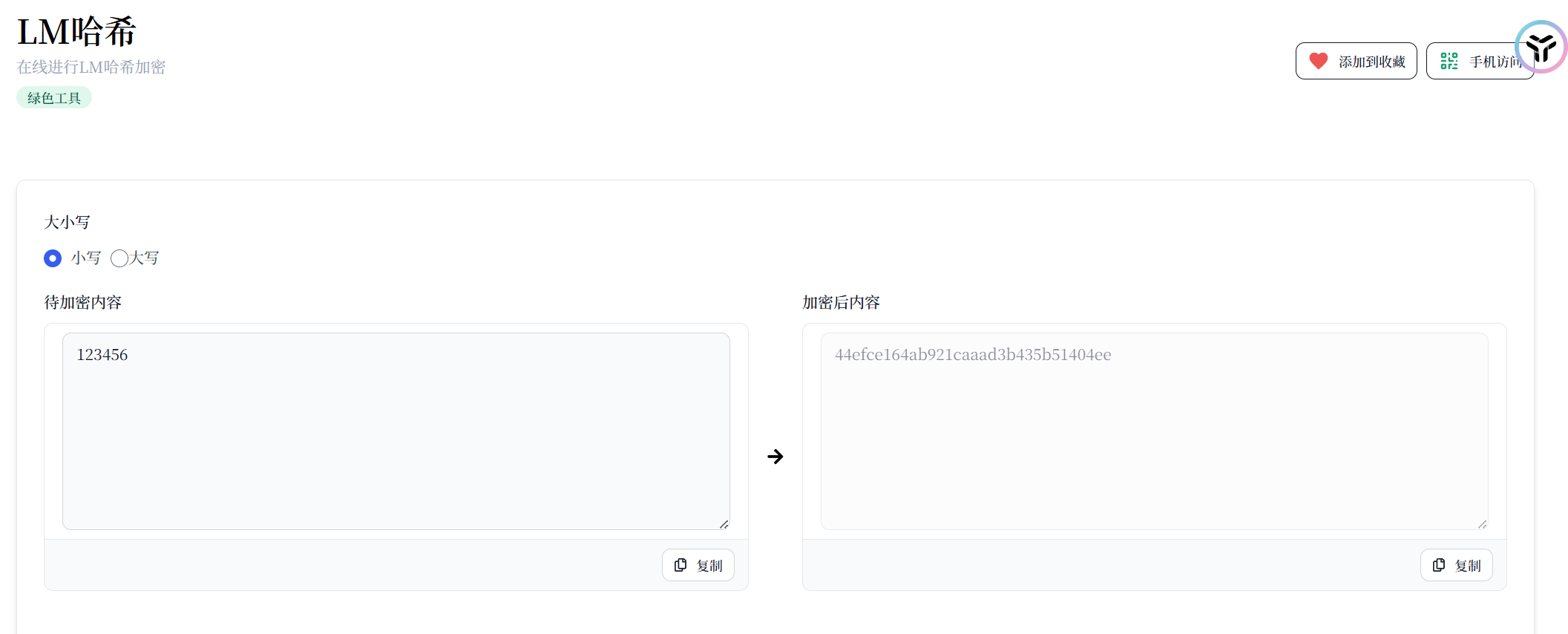
值为
1 | 44efce164ab921caaad3b435b51404ee |
由上述可知aad3b435b51404ee为空密码,我们只破解前16位即可
1 | 44efce164ab921ca |
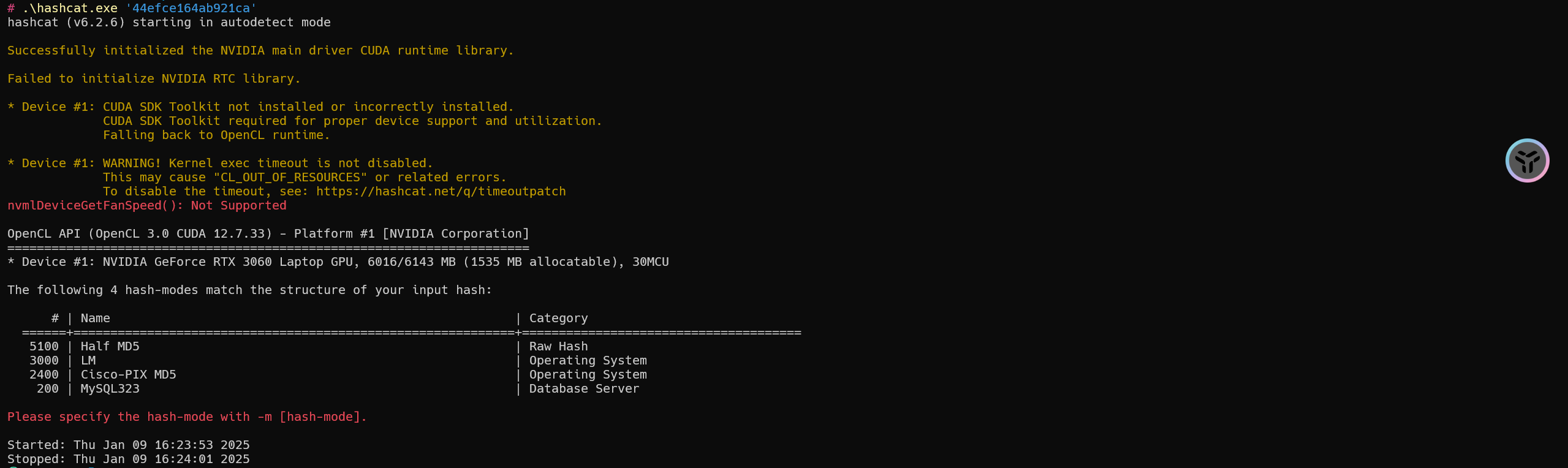
示例
1 | hashcat -a 0 -m 3000 '44efce164ab921ca' "E:\400W常用密码(整理).txt" |
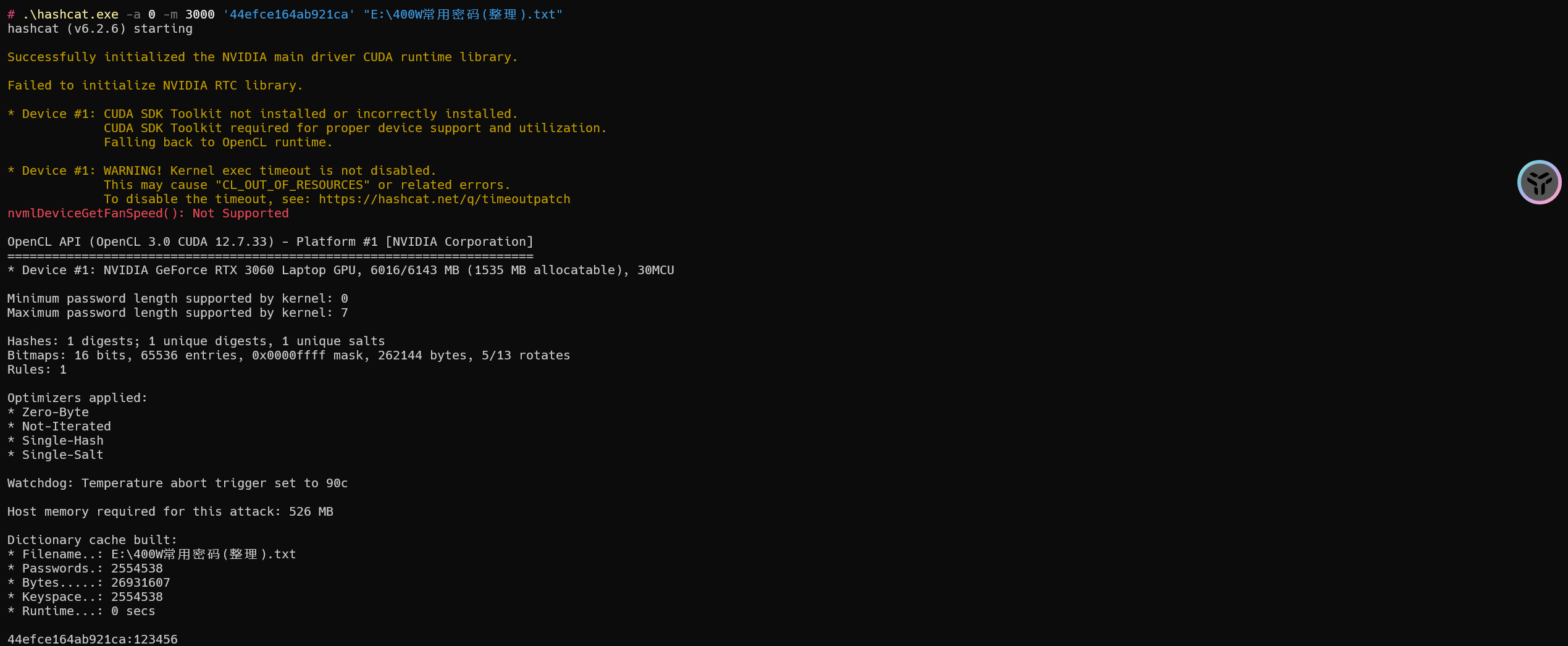
密码为:123456
NTLM和LM可看[3.1 本地认证——NTLM哈希和LM哈希_lm(lan manager)哈希-CSDN博客](https://blog.csdn.net/GloryGod/article/details/132478730#:~:text=LM Hash 的全名为”LAN Manager Hash”,是微软为了提高 Windows操作系统的安全性而采用的散列加密 算法,其本质是DES加密。 尽管,Hash较容易被破解,但为了保证系统的兼容性,Windows只是将LM Hash禁用了(从Windows vista和 Windows Server2008版本开始, Windows操作系统默认禁用 LM Hash)。)
破解JWT
去这里生成一个加密的jwt
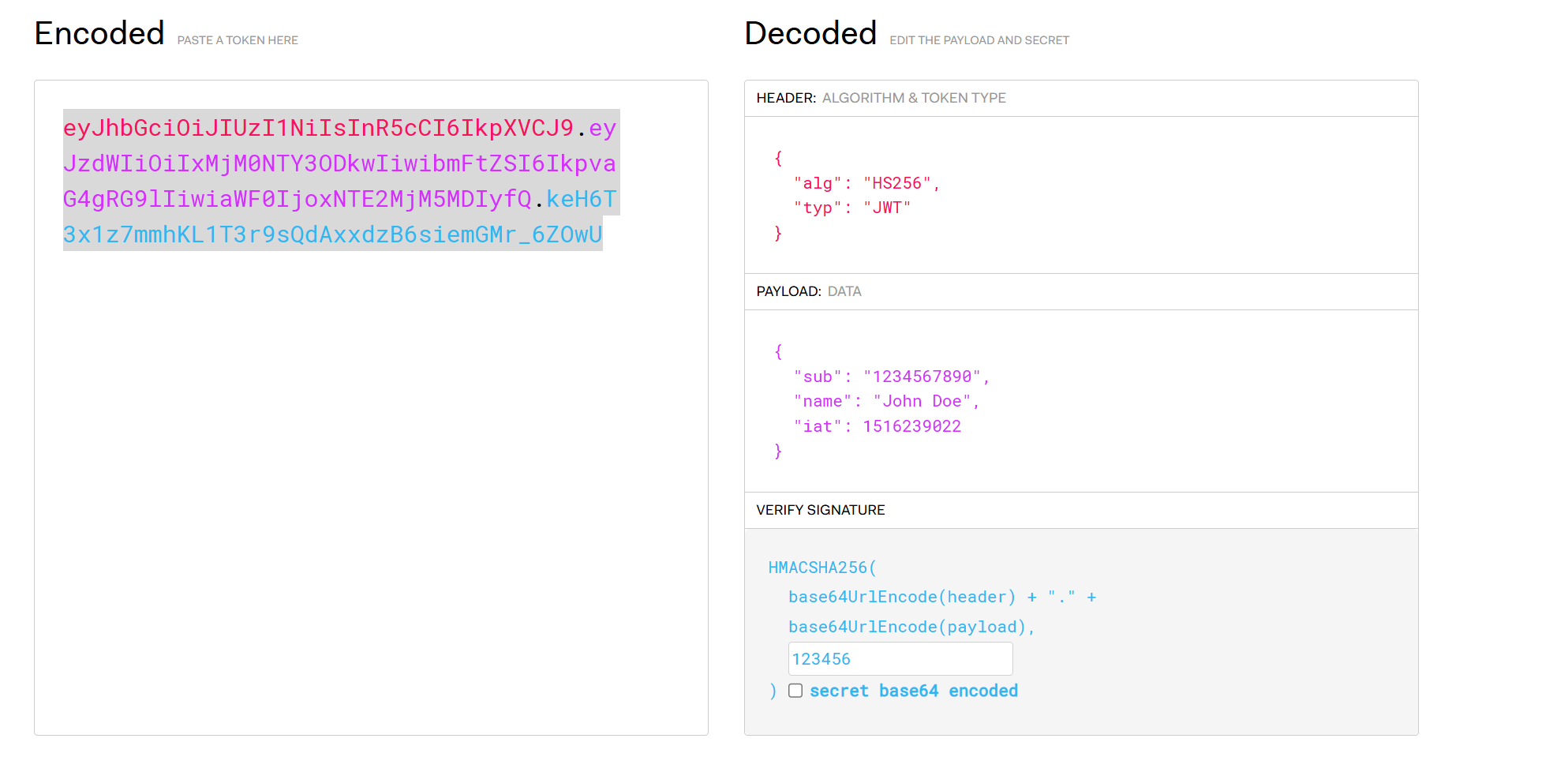
值为
1 | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.keH6T3x1z7mmhKL1T3r9sQdAxxdzB6siemGMr_6ZOwU |
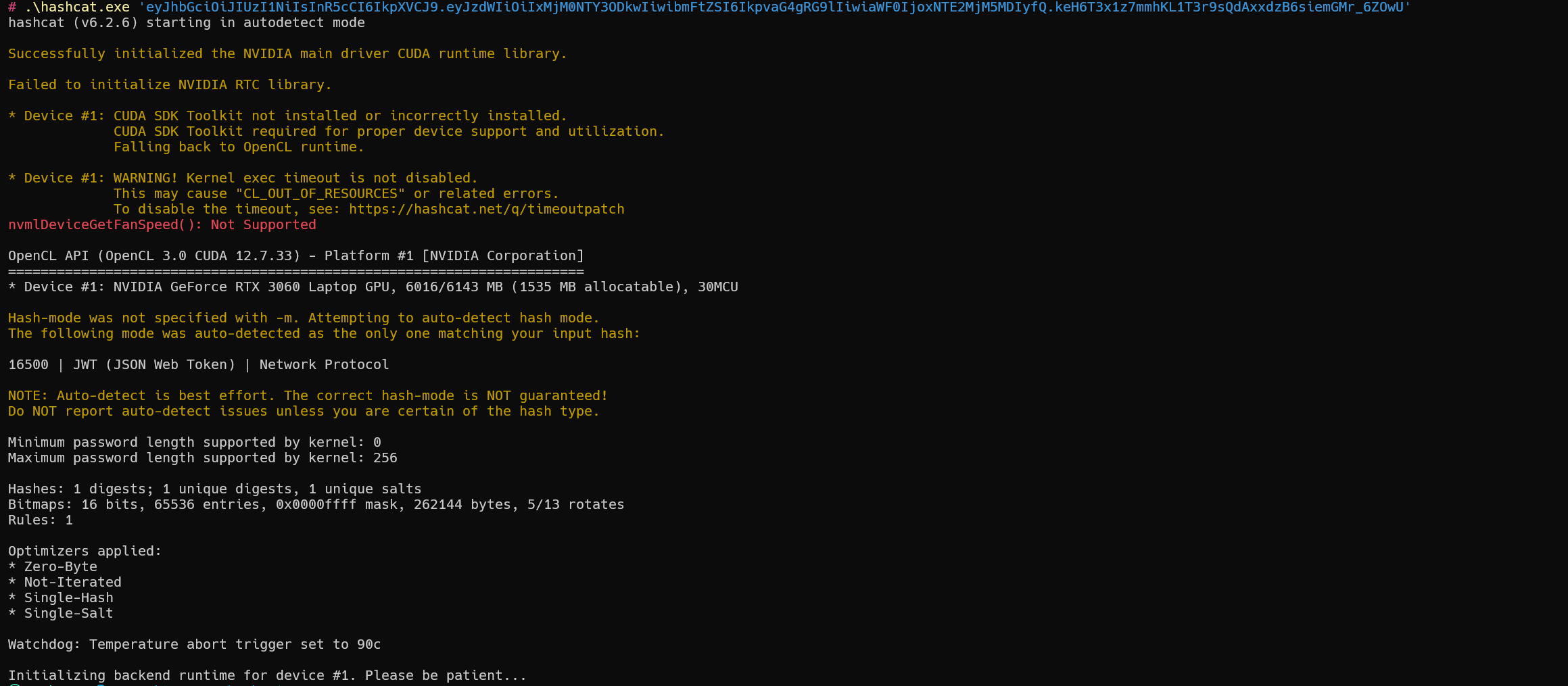
示例
1 | hashcat -a 0 -m 16500 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.keH6T3x1z7mmhKL1T3r9sQdAxxdzB6siemGMr_6ZOwU' "E:\400W常用密码(整理).txt" |
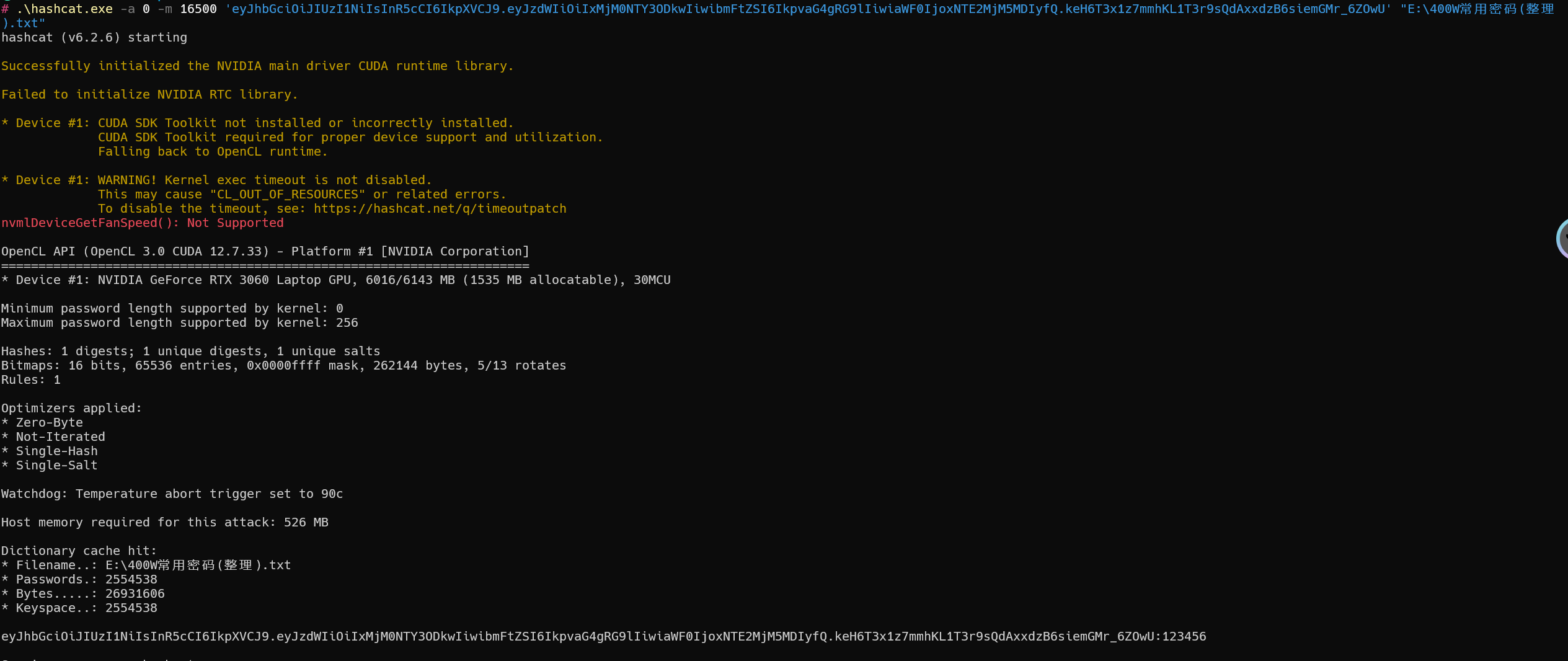
密码为:123456
破解PDF
先使用John the Ripper获取hash值

值为
1 | $pdf$4*4*128*-3904*0*16*26ac7a3c91bd422286fb1c081e5e4ae3*32*5014f14464acbaae9c3dce5e1e3f3d52d8d298b0b04543b03b4a1aee0f26b84d*32*c431fab9cc5ef7b59c244b61b745f71ac5ba427b1b9102da468e77127f1e69d6 |
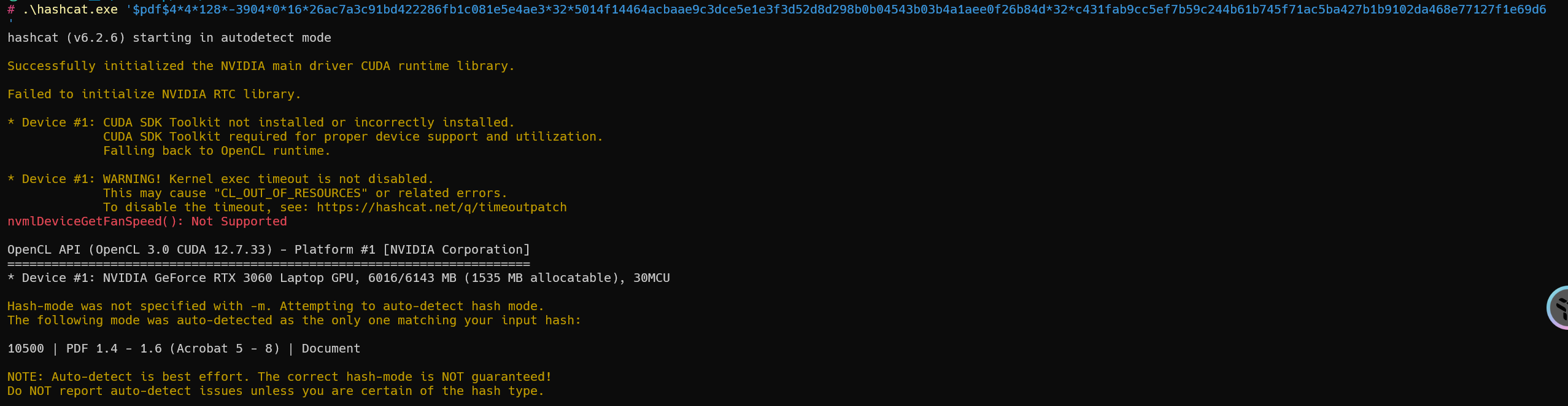
示例
1 | hashcat -a 0 -m 10500 '$pdf$4*4*128*-3904*0*16*26ac7a3c91bd422286fb1c081e5e4ae3*32*5014f14464acbaae9c3dce5e1e3f3d52d8d298b0b04543b03b4a1aee0f26b84d*32*c431fab9cc5ef7b59c244b61b745f71ac5ba427b1b9102da468e77127f1e69d6' "E:\400W常用密码(整理).txt" |
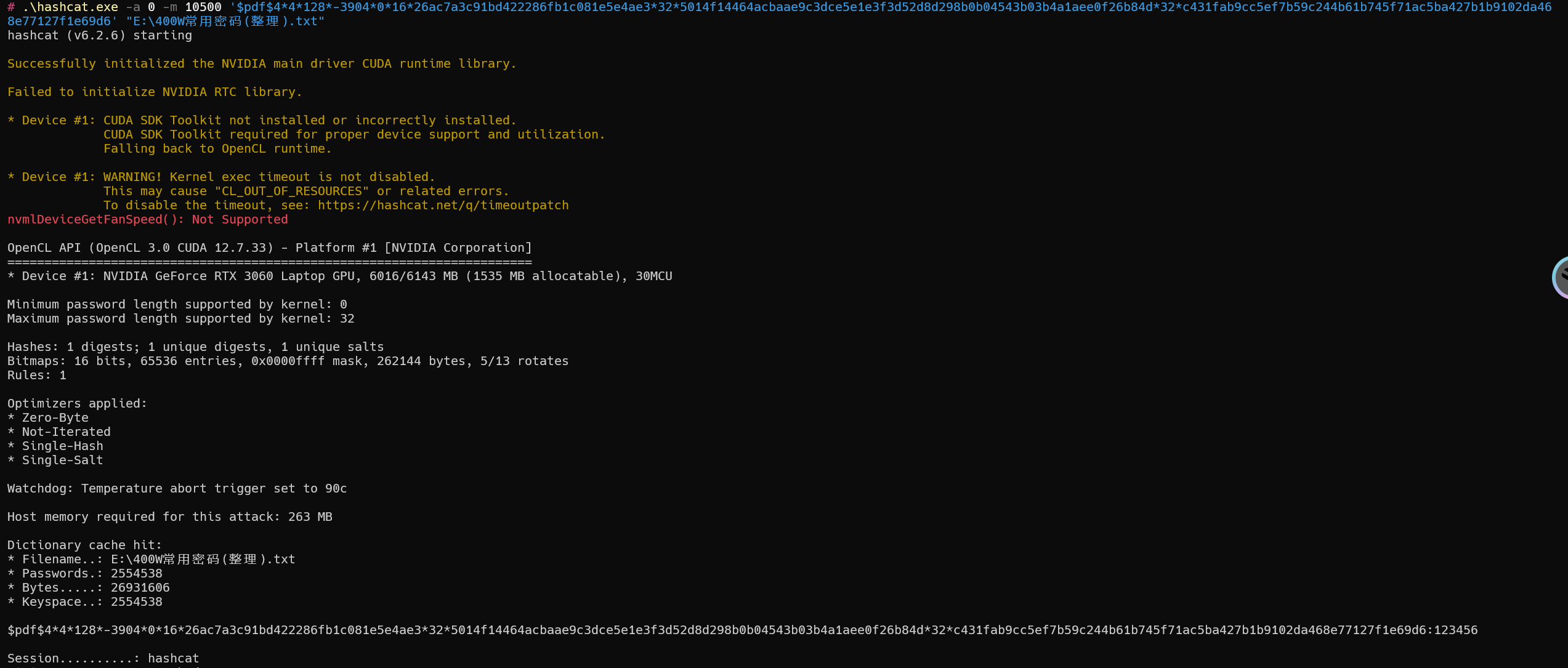
密码为:123456
总结
官方的话语是
- 世界上最快的密码破解工具
- 世界第一个也是唯一一个内核规则引擎
- 开源,免费,多支持
- 支持分布式
hashcat对于我来说,有获取到一些有特征性的Hash在一些解密平台没有数据的,但是自己知道特定格式的情况下有奇效
